#224: Join us on a Python adventure back to 1977
Special guest: Calvin Hendryx-Parker
Live stream
Michael #1: AWSimple
- by James Abel
- AWSimple is a more object oriented interface on top of boto3 for some of the common “serverless” AWS services: S3, DynamoDB, SNS, and SQS.
- Features:
- Simple Object Oriented API on top of boto3
- One-line S3 file write, read, and delete
- Automatic S3 retries
- Locally cached S3 accesses
- True file hashing (SHA512) for S3 files (S3's etag is not a true file hash)
- DynamoDB full table scans (with local cache option)
- DynamoDB secondary indexes
- Built-in pagination (e.g. for DynamoDB table scans and queries). Always get everything you asked for.
- Can automatically set SQS timeouts based on runtime data (can also be user-specified)
- Caching: S3 objects and DynamoDB tables can be cached locally to reduce network traffic, minimize AWS costs, and potentially offer a speedup.
Brian #2: coverage and installed packages
- I’ve covered coverage.py a lot on Test & Code, starting with episode 12, and even talked about it on episode 147, and many others.
- Except there’s something I missed, hidden in plain sight, all this time.
coverage --source, as well aspytest --covif usingpytest-covplugin, is not just a path.- “You can specify source to measure with the
--sourcecommand-line switch, or the[run] sourceconfiguration value. The value is a comma- or newline-separated list of directories *or package names*. If specified, only source inside these directories or packages will be measured.” - coverage.py docs, (emphasis mine) - Up to now I was doing this trick I picked up from I don’t remember where I would run coverage from the top level project directory, specify the source as the project source, and set a
[paths]setting in .coveragerc, thesourcesetting to both the project source and the site-packages directory. - Then the report would show the coverage of the source code, even though it was the site-packages code that was running.
- That trick is still nice to specify the output as your project directory, which is usually a shorter relative path.
- However, it’s not essential. You can just specify the source as the package name, without the above trick, and coverage will report the coverage of the installed package. That is usually good enough.
- Super cool
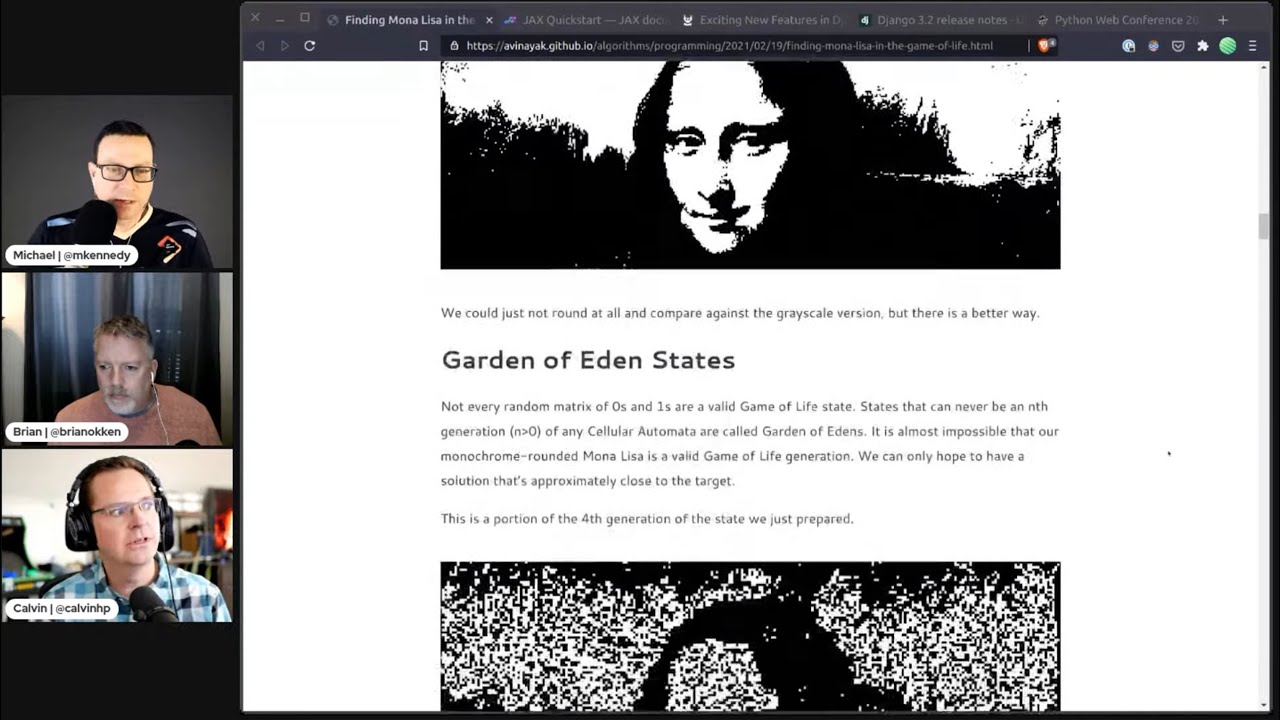
Calvin #3: Finding Mona Lisa in the Game of Life with JAX
- by Atul Vinaya
- Lots of great code examples
- Showcases the speed increase you can get using JAX on a GPU vs CPU unvectorized
- Initial implementation took days of CPU time to get a rough result
- JAX compiles numpy to highly vectorized code to run on a GPU
- Requires some refactor of the code to optimize for a highly parallel run on GPUs
- Post includes link to notebook used for the project
- “Running ~1000 iterations for a 483px wide Mona Lisa on the google colab GPU runtime only takes around 40 seconds!”
Michael #4: Python Package Index nukes 3,653 malicious libraries uploaded soon after security shortcoming highlighted
- From Mark Little
- Recall Google’s Python goal was around PyPI security.
- Related (from @tonny) Poison packages – “Supply Chain Risks” user hits Python community with 4000 fake modules
- PyPI has removed 3,653 malicious packages uploaded days after a security weakness in the use of private and public registries was highlighted.
- “Developers are often advised to review any code they import from an external library though that advice isn't always followed.” ← yeah
- Last month, security researcher Alex Birsan demonstrated how easy it is to take advantage of these systems through a form of typosquatting that exploited the interplay between public and private package registries.
- Birsan set out to see whether he could identify the names of private packages used inside companies and create malicious packages using those library names to place in the public package registries – the indexes that keep track of available software modules.
- The names of private packages turned out to be rather easy to find, particularly in the Node.js/JavaScript ecosystem because private package.json files show up rather often in public software repositories.
- So Biran crafted identically named libraries that he designed to sneak system configuration data through corporate firewalls.
- The challenge then became getting applications that require private libraries to look for those file names in a polluted public source. As it turns out, it's common for corporate software developers to rely on a hybrid configuration for their applications, one that references private internal packages but also supports fetching dependencies from a public registry, in order to ensure packages are up-to-date.
- The companies that Birsan managed to attack with this technique include Apple, Microsoft, Netflix, PayPal,Shopify, Tesla, Uber, and Yelp. And for his efforts, he has been awarded at least $130,000 from bug bounty programs involving these firms.
- Birsan's success in carrying out such attacks should set off alarm bells. Software supply chain attacks present a higher degree of risk than many threat scenarios because they have the potential to affect so many downstream victims
- Makes me want to setup devpi + devpi-constrained just for internal projects.
- What to do?
- Don’t do mass bogus uploads like this to prove your point. We appreciate the message you are trying to deliver, but it’s already been documented so you are just making distracting work for other people who could more usefully be doing something else for the project.
- Don’t choose a PyPI package juat because the name looks right. Check that you really are downloading the right module from the right publisher. Even legitimate modules sometimes have names that clash, compete or confuse.
- Don’t hook internal projects to external repositories by mistake. If you are using Python packages that you haven’t published externally, then the one thing you can be sure of is that all external copies of “your” package are imposter modules, probably malware.
- Don’t blindly download package updates into your own development or build systems. Test and review everything you download before you approve it for use. Remember that packages typically include update-time scripts that run when you do the update, so malware infections could be delivered as part of the update process, not of the module source code that ultimately gets installed.
Brian #5: python-adventure
- Brandon Rhodes
- "This is a faithful port of the “Adventure” game to Python 3 from the original 1977 FORTRAN code by Crowther and Woods (it is driven by the same
advent.datfile!) that lets you explore Colossal Cave, where others have found fortunes in treasure and gold, though it is rumored that some who enter are never seen again. “ - “For extra authenticity, the output of the Adventure game in this mode,
python3 -m adventure, is typed to your screen at 1200 baud.” - “Colossal Cave Adventure is the first known work of interactive fiction and, as the first text adventure game, is considered the precursor for the adventure game genre. “ - wikipedia
- related:
- Zork, 77-79, also an adventure game, was inspired by Collossal Cave Adventure, 75-77
- Zork on Chuck - Brian’s a Chuck fan
- Brandon, can we have Zork also?
- side note:
- Closest I got was Dungeons of Daggorath on TRS-80. Not text based. Early 80’s
Calvin #6: Exciting New Features in Django 3.2
- From Haki Benita
- Upcoming LTS Release in the 3 series
- Expected in April
- Post highlights some interesting new features that you might not have noticed
- New Features
- Covering Indexes in Postgres support (performance plus!)
- Timezones are hard and TruncDate now helps keep you from pulling out the foot cannon
- JSONObject DB Functions, helping the unstructured data world keep using Postgres
- Signal.send_robust() now logs exceptions so you don’t have to!
- The new QuerySet.alias() method allows creating reusable aliases for expressions (Performance!)
- The new
displaydecorator makes creating calculated admin fields cleaner - Value Expressions Detects Type, more cleaning up to allow the ORM to figure it out
- Notable missing feature is Async ORM, but this will be awesome when it lands
- More are listed on the Django 3.2 Release Page
Extras:
Michael:
- Is Python on Mars?
- FastAPI Website course is out: talkpython.fm/fastapi-web
- Are you thinking of going to PyCon 2021? Over at Talk Python, we're giving away 5 tickets to the event: talkpython.fm/pycon2021
- Be sure to join us @ pythonbytes.fm/youtube
- Got a chance to speak to the medical field about Python and programming superpowers on the Finding Genius podcast.
Calvin:
- DjangoCon Europe 2021 CFP is Open until 4/1 https://2021.djangocon.eu/talks/cfp/
- Python Web Conf 2021
- 4 Tracks this year
- 60 Amazing Speakers (almost 20% women)
- Tickets
- Professional $199
- Student $99
- Grants Available!
Joke:
/** Logger */
private Logger logger = Logger.getLogger();
// This is black magic
// from
// *Some stackoverlow link
// Don’t play with magic, it can BITE.
# For the sins I am about to commit, may Guido van Rossum forgive me
// Remove this if you wanna be fired
}
catch(Exception ex)
{
// Houston, we have a problem
}
int getRandomNumber()
{
Return 4; // chosen by fair dice roll.
// guaranteed to be random.
}
https://twitter.com/LinuxHandbook/status/1368974401979383810
Episode Transcript
Collapse transcript
00:00 Hello and welcome to Python Bytes, where we deliver Python news and headlines directly to your earbuds.
00:04 This is episode 224, recorded March 10th, 2021.
00:08 I'm Michael Kennedy.
00:10 And I'm Brian Okken.
00:11 And I'm Calvin Hendryx-Parker.
00:12 Hey, we have a special guest, Calvin. Welcome to the show.
00:15 Hey, thanks for having me.
00:16 Yeah, it's fantastic to have you here.
00:18 Always great to have a fresh face.
00:20 I believe it's been about a year since you were on the show previously.
00:23 Is that right?
00:23 I think almost exactly a year, yes.
00:25 Yeah, YouTube reminded me that it was one of the first videos of this whole Python Bytes that we put up there.
00:31 Before we were live streaming, we'd record it and then put it up.
00:34 That was so last year.
00:35 I know. I mean, Python Bytes, you guys have really upped your game.
00:38 I'm super proud of y'all.
00:39 Yeah, it's so 2020.
00:40 Yeah, yeah, yeah.
00:41 We got our broadcast studio working right here in Portland, Oregon.
00:45 Super, super nice.
00:46 Speaking of nice, I want to do a follow-up.
00:49 You know, what's nice, Brian, is so often our guests, they send us all these items.
00:54 And, you know, we'll mention something and we'll think this is like the first time I've heard of this.
00:58 And they're like, and here's the 10 other amazing things that you've never heard of.
01:01 Yes.
01:01 And so this is a little bit of a follow-up along that.
01:04 Before actually, I realized before I get into that though, Calvin, maybe you want to just do a quick, who are you?
01:09 It has been a year.
01:10 It has been a year.
01:11 Everyone's going to remember who you are.
01:13 Sure, sure.
01:13 I'm Calvin Hundix Parker.
01:14 I'm co-founder and CTO of Six Feet Up.
01:16 And I'm also the co-founder of the IndiePy group here in Indianapolis, the Python user group.
01:21 And we are also the organizers of the Python web conference, which I'll talk about later.
01:24 So that's kind of a quick rundown of me.
01:26 You're that company that hands out Python jersey shirts.
01:28 Oh, yeah.
01:28 We do some killer swag.
01:30 Yeah, yeah, for sure.
01:31 That's a cool conference.
01:32 Be fun to talk about that in a little bit.
01:34 So the first thing, though, that I do want to talk about over here is AWS Simple.
01:39 We talked about Boto-type definitions, I think it was.
01:43 And then someone mentioned that Boto-type definitions has kind of been deprecated, ignored, and so on.
01:48 And so they pointed us at this mypy live generated version that we talked about last week.
01:53 And also, we got a message from James Abel, who said, hey, I built this cool library called AWS Simple.
02:02 And I got it all flowed together to get all the S's to fit in there, AWS Simple.
02:05 And the idea is that it's a typed wrapper around the AWS API.
02:12 And if you recall, I kind of was harsh on the Boto 3 API.
02:15 And I can buy that because there's just zero discoverability on how it works.
02:19 There's like inconsistencies on how you pass parameters.
02:22 Sometimes you pass them by name.
02:24 Sometimes you pass them as dictionaries with names in the dictionary.
02:27 Just a lot of stuff going on there.
02:28 And it's really not discoverable.
02:30 And so this one also is one of those libraries that's meant to help with that.
02:34 So it's a simple API for basic services like S3, DynamoDB, their hosted NoSQL database, simple notification service, simple queuing service.
02:45 I don't know if you guys have been to AWS lately, but you go to your console and it says, here's the two things you've recently visited.
02:49 See the rest.
02:50 And it like, it scrolls.
02:52 There's a lot.
02:53 So this is clearly not everything, but it is some common ones, especially around S3, I think.
02:58 And it's also maybe the kernel of other things, right?
03:00 People often ask me, hey, what project could I contribute to?
03:03 Well, if you're like, I would really love to have simple email service integrated with this.
03:06 Like, well, you know, it probably is easy to add like one more service.
03:10 So some of the features include a nice object oriented API on top of Boto 3 with proper type definitions and classes and static things that all the static type checkers and the editors all know about and love.
03:22 You can write a really simple, like one liners to do S3, read, write, deletes.
03:27 It has automatic retry for S3.
03:29 It has caching.
03:30 So for example, it will, when you get a file or upload a file, it will hash that result.
03:36 And basically if you try to get it again, it'll say, let me check the E tag.
03:41 That's the way web browsers and servers exchange.
03:44 Like here's the sort of history or the version of the file.
03:47 And it'll check, has this thing changed or not?
03:49 And so it'll not download the S3 file if it hasn't changed.
03:52 And you ask, it'll just use like the last version that got since it touched it.
03:55 Things like that.
03:56 Some DynamoDB full table scans, secondary indexes and pagination.
04:01 So there's some simple examples like my S3 access.
04:04 And then maybe if you could do DynamoDB, create a DynamoDB access and just put an item or get an item.
04:11 And off it goes.
04:12 Really, really simple.
04:13 You know, as you would imagine something with a name like AWS Simple has.
04:16 But, you know, it's just one more thing around AWS APIs that I think is pretty interesting.
04:21 What do you guys think?
04:21 I kind of expected a bullet to bury in there saying AWS Simple is not simple because this is a massive undertaking to try and make something like this simple.
04:29 Yeah, absolutely.
04:30 I totally agree with that.
04:31 I mean, it's pretty neat.
04:32 Over in their documentation, they've got a little more examples and a quick start guide and how to use it and so on.
04:38 But yeah, it's pretty easy.
04:40 You just do like S3, create bucket, S3, write string to this key.
04:43 Go on.
04:44 It's quite easy.
04:45 So if you're struggling with the AWS APIs, this is the cool project.
04:50 And again, I think it's pretty limited to just a couple of the services.
04:53 So it's somewhere that if you've got your favorite service and you want something like this for it, you know, reach out, James, and add it.
04:59 Yeah, and all of the services could be added.
05:00 And then AWS Simple could be as complex as everything else.
05:03 Exactly.
05:04 Like I can barely install this thing anymore.
05:07 It's really legit.
05:09 Yeah, they're trying to become the AWS APIs for humans, kind of like requests for HTTP, URLib.
05:15 Yeah, maybe.
05:16 I mean, Boto3 was kind of like that too, right?
05:18 Well, again, the S3 APIs, they've changed names.
05:22 They're inconsistent.
05:23 It's really hard to like parse.
05:24 Sometimes as a human, like the uploading process of like multi-part uploads.
05:28 If you're not into the web, this could be really daunting.
05:30 Sounds like this is a great way to enter this space and not have to learn all that stuff.
05:34 I can't just do this thing.
05:36 I got to create a waiter and I got to wait on the thing and so on.
05:39 Yeah, absolutely.
05:39 Dean Langsom up there in the live stream said, it's amazing to me how many of the most accessed
05:45 APIs in the world need third-party packages to make them useful.
05:48 Yeah.
05:49 I mean, if it weren't such a small little rinky-dink company, if they could hire a bunch of developers
05:53 to work on this, like, oh, wait, no, it's Amazon.
05:55 No, I totally agree with you, Dean.
05:57 That's funny.
05:57 All right.
05:58 Yeah.
05:59 So AWS Simple, check it out if that appeals to you.
06:01 Brian, what you got for us?
06:02 Well, I was going to, how do we do this?
06:06 Oh, yep.
06:06 We both clicked.
06:07 Sorry about that.
06:08 It was a race car.
06:09 So I learned something new the other day.
06:13 And I learned something new about something old.
06:15 So I've used coverage.py a lot over the past several years.
06:22 And I've even covered it a lot on the Test and Code podcast a couple times.
06:26 Covered it on the podcast.
06:28 Yep.
06:29 That's a meta joke.
06:30 Anyway, there's something I missed the whole time.
06:33 So there's a source thing.
06:36 So you can tell coverage where the source code is, where the source is for your, whatever you're
06:40 covering.
06:41 And hidden in here is the source can be, the source is either directories or packages.
06:50 It's the or packages I never saw before.
06:53 Oh, that's cool.
06:54 So why this is significant, and apparently this has been here the whole time, and I just missed
06:58 it, is there was a workaround.
07:01 So if I, if I'm testing, if I've got, if I'm developing a package and I want to test
07:06 it as an installed package, I install it.
07:09 And then I run the tests against the installed package.
07:12 But how do I run coverage against that?
07:14 And there was an old trick to, and it, I guess it still is works, is to use the paths option
07:22 within coverage to say these two paths are identical.
07:26 So you could say the actual source code directory is identical to the site packages directory
07:32 so that it, it, it kind of lines everything up and then it reports, even though it's measuring
07:36 the coverage on the installed package, it reports it as if it was sitting in the source directory.
07:42 And so I've been doing that in the past.
07:44 And that still is a good idea so that the output is readable, but it isn't required.
07:49 You can just pass in the name of your package without the dot PI or anything, or if it's
07:55 just a file, but just the name of the package and it just reports it.
07:59 And yeah, anyway, I just figured that maybe some people out there have missed that also.
08:04 It's very handy.
08:05 Well, you might wonder like, why are you testing packages?
08:07 I don't need the coverage of requests when I use it.
08:10 I just know that I use it and we're all good.
08:12 Well, if you're developing requests, you might want to come.
08:15 Yes, exactly.
08:16 Or, you know, it may well be that you're building your application out of several packages that
08:23 you control and you kind of want to keep them separate for reuse, but you might also want
08:26 to know like how much am I interacting with that one, right?
08:29 Oh, that's a cool use to say really what, how, how much am I interacting with the package?
08:34 You could run coverage on that.
08:35 Yeah.
08:35 If it's zero, take it out of your requirements.
08:38 That would be super nice.
08:40 Yeah.
08:41 This is really cool.
08:42 Yeah.
08:42 Also, I guess when one of the reasons why that might be handy is if, if they change,
08:47 drastically change an API, like go to a new dot, you know, like a three dot something to
08:53 four dot something.
08:54 What is the API change?
08:56 And you could check to see if you're even using that API or that entry point.
09:01 That might be good.
09:01 Oh, that's interesting.
09:02 Yeah.
09:02 Yeah.
09:02 That part was like a breaking change, but I don't care.
09:05 Yeah.
09:05 Okay.
09:05 Like I can really see the, there's a huge use case here though, for old code bases where the
09:10 developers aren't there anymore and there's been dependencies brought in and you don't
09:13 know exactly what's being used.
09:14 So this is like super nice to be able to do that.
09:17 Yeah.
09:17 And of course, as a reminder, you can have as many of these as you want to.
09:21 So if you, if you're wanting to measure several packages, you can add multiple source flags.
09:27 And if you're using pytest-cov, it's the cov flag.
09:31 So you, which is identical.
09:33 I'm not sure why they used cov and dash cov instead of dash source, but there you go.
09:37 Interesting.
09:38 Okay.
09:38 Yeah.
09:38 Yeah.
09:39 Super cool.
09:39 Super cool.
09:40 So Calvin, I didn't know that you were an artist.
09:42 I wish maybe more of a machine learning artist, but machine learning artists.
09:47 This really interesting article came up on my like newsfeed last week, which was finding
09:52 Mona Lisa in the game of life with Jax.
09:54 And so there's kind of three interesting things there, like Mona Lisa, game of life, and then
09:58 Jax.
09:58 The author was attempting to find if he could start with a starting set of points on a game
10:05 of life.
10:05 If you're not familiar with game of life, there's whole Wikipedia articles about that.
10:10 But if you could basically seed an initial game of life and after so many generations have
10:16 it show you a picture.
10:17 So he actually started with the Mona Lisa and kind of went through what it would take to go
10:22 from, you know, a game of life running all the kinds of constraints that happen in that.
10:26 But this seems like a really interesting machine learning problem.
10:29 And that's cool.
10:29 So it like our it randomly runs the game of life.
10:33 But then the ML says, oh, that's starting to look like Mona Lisa.
10:37 More of that.
10:38 Well, it's more of that.
10:39 I'm going to run a generation of game of life and then reset.
10:42 I'm going to invert some pixels again and go again until I can generate what is my target
10:48 picture.
10:48 And it took a lot of CPU cycles.
10:50 He basically wrote a simple single threaded version of this in Python.
10:53 And there's a there's Python notebooks included with the GitHub links in here.
10:56 But it took days of CPU time for him to run the initial four generations to see if he could
11:02 even make this be possible.
11:04 And then kind of went with any machine learning project.
11:07 It's really important to understand like the preparation of your data before you kind of
11:11 go dive in.
11:12 So what I also thought was interesting in here is he talks about the preparation of the data
11:15 kind of down here, pre-processing, you know, using pill to understand how to generate
11:20 that target first, give the game of life algorithms a chance of getting it correct, came into like,
11:27 you know, really half tones would work better because there's some constraints around game
11:29 of life that the whites can't be contiguous to contiguous because they'll they'll kill
11:34 each other and ends up being all black.
11:36 And but at the end, the kind of goal of this was how fast can we now do it?
11:40 Take the single threaded Python example, which took hours or days of CPU.
11:45 Can we actually do it on a GPU?
11:47 And so there's a JAX library, which is a machine learning library in Python that allows you
11:52 to actually like super parallelize the problem.
11:54 So if you can actually slice the problem up shows kind of example here in pictures, which
11:58 is kind of nice for a person who doesn't do a lot of machine learning.
12:00 Yeah, they actually kind of show you what the process looks like and hyper parallelize this
12:05 basically in 40.
12:07 He went from days of CPU time down to 40 seconds to get through the first camera.
12:12 What was the final time?
12:13 40 seconds.
12:14 It was that.
12:15 Yeah.
12:16 Yeah, it was ridiculous.
12:17 It's like so a thousand iterations.
12:18 So the first one was for four generations took days.
12:21 The next one where he did it with JAX was a thousand iterations took 40 seconds on a Google
12:27 Colab GPU.
12:28 So JAX is basically a Python library.
12:30 I've got a quick little quick start over here.
12:32 Neat library that actually you kind of have to alter your brain to a little bit to how you
12:37 code so that you can code in a way that can be hyper parallelized across all the GPUs.
12:42 I mean, for people who aren't familiar with GPUs, which you may not be because good luck
12:45 getting a GPU right now.
12:46 They're unobtainium at this point.
12:48 But if you did have a GPU, you can take advantage of those, you know, how many cores are in some
12:54 of these modern GPUs, like thousands in the new, like in video.
12:57 Every time that I try to think about and try to conceptualize, like how fast and how much
13:01 these things can do, I'm like, whatever that is, it's probably off by 10 or many, many more.
13:05 Yeah.
13:05 Factor of 10, just like ramp that up to beyond what you can think is reasonable.
13:09 It's right.
13:10 You think of we've got a, you know, half a million polygons on the screen and we're going to
13:14 draw that.
13:15 Oh, we're actually going to do that 200 times a second.
13:17 Right.
13:18 So what's interesting is if you are doing some machine learning experimentations, learning
13:22 a tool like JAX may actually help you speed up your iteration so you actually can get some
13:26 useful results out of it.
13:27 Because a lot of machine learning is kind of picking out what your algorithm based algorithm
13:31 is going to be.
13:31 But you have to run it enough to know whether your algorithm is getting you the results
13:35 you expect.
13:36 So being able to run through those algorithms quicker with a tool like JAX, I think would
13:39 be super beneficial.
13:40 Yeah, absolutely.
13:41 That's super neat.
13:43 And I think the biggest takeaway here is JAX, actually.
13:46 Yeah.
13:46 That was.
13:47 Yeah.
13:47 The end goal was like, yeah, can we talk about JAX?
13:50 Because that's a really cool library.
13:51 Well, and a cool logo, by the way.
13:53 Yeah.
13:53 Yeah.
13:54 Yeah.
13:55 I love it.
13:55 The logo is super cool, actually.
13:56 I like it.
13:57 Yeah.
13:57 But definitely.
13:58 And I think they have support for Tensor processing units as well.
14:01 So not only GPUs, but if you're doing like TensorFlow stuff, Tensor GPUs or Tensor processing
14:06 units, so you can take advantage of those as well.
14:07 Yeah.
14:08 Okay.
14:08 Super neat.
14:09 Super neat.
14:09 Super neat.
14:09 I want to talk about something that's not as neat.
14:12 Maybe it'll get you excited, but in the wrong way.
14:15 This one was sent over by my friend, Mark Little, fellow Portlander, and a follow-up related
14:20 one sent over by Tony.
14:22 So link into a couple of articles here.
14:24 And recall, we talked about Google coming on as the visionary sponsor.
14:29 One of their primary goals that they wanted was to improve the package security.
14:33 You think about some of the things that have happened recently that are super scary.
14:38 One, the Outlook catastrophe that 60,000 companies have been taken over.
14:44 And then the SolarWinds one as well.
14:46 And I think they're somewhat related, even though they're not the same origin or the same type
14:50 of hack.
14:50 The SolarWinds one is one of these supply chain vulnerabilities and these breaches, right?
14:55 It's one thing to say, I'm going to protect against somebody breaking into my website.
14:59 I'm going to run the proper firewalls, low privileges, everything's patched, et cetera, et cetera.
15:04 That might still not be enough, but that's like a good start.
15:07 But do you think about, well, next time you install the new version of package, whatever,
15:13 what if it was influenced with some kind of negative package that had some vulnerability
15:18 that then got into your servers and then went on?
15:20 Like the supply chain story around all of these package management places is scary.
15:26 I think that's not what happened to SolarWinds.
15:28 They just had the password, SolarWinds123.
15:30 That's a different type of problem.
15:32 But it highlights-
15:33 Those aren't interns.
15:34 Exactly.
15:35 Exactly.
15:35 But the problem that it might be untrustworthy to install all of our beautiful open source
15:42 things.
15:43 I don't know.
15:43 It's very scary.
15:44 Like, what do you guys think about this?
15:45 It seemed like this went even a level deeper.
15:47 There wasn't even scary to install the open source things.
15:50 It was dangerous to install your own private package names if someone knew about them and
15:55 had put them into a public repository with a newer version.
15:58 Yeah.
15:59 So let me read the titles here for people who are listening.
16:02 The Python package index nukes 3,653 malicious libraries uploaded soon after a security shortcoming
16:08 is highlighted.
16:10 And the other one is poison packages, supply chain risks, users hit Python community with
16:16 4,000 fake modules.
16:18 And these are basically the same.
16:19 I don't know if like one's rounding up or whatever, but- or one's counting multiple incidents.
16:23 But the idea is there's this form of type squatting that's pretty sketchy.
16:28 So we've covered this before where if you have- maybe I want to use the audio library asteroid
16:34 singular, but then somebody puts asteroids plural, that is a virus.
16:38 And it could just as well have exactly the same code plus the virus.
16:41 So it looks like it works.
16:43 You wouldn't even know that it's not working, right?
16:44 Yeah.
16:45 And that's quite the problem.
16:46 But here the highlight is what's it called?
16:49 Like I think one thing was calling it evil twin.
16:52 Another, this is a research by Alex Beerson.
16:56 And basically there's a lot of people who are using private package repositories, right?
17:02 Like DevPy and things like that, Artifactory, where you have a local one.
17:06 But if you ask for something public, you can just ask your local one and the local one will
17:10 go out and ask the public one.
17:12 So as you were hinting at Calvin, the problem is what if I just have like data layer or e-commerce
17:18 or like some random thing that might be an internal package name?
17:22 Maybe if it's what I think the real problem was they were saying, if you don't secure your
17:27 server right, you just post a higher version on the public one than on, on the local one.
17:33 And it'll go, oh, well, there's a newer one over there.
17:35 I better get that.
17:36 And we'll just go grab the virus.
17:38 I'm also surprised that folks aren't pinning the versions of their internal packages as well.
17:42 Because I would, this would satisfy solving that problem is if you had like we use pip-tools,
17:47 pip compile to make sure we got hashes and versions for every dependent package.
17:53 But yeah, if you didn't do that, you were absolutely susceptible to this.
17:57 Yeah.
17:57 So just people check this out.
17:59 It's, it looks a little scary.
18:01 I, you guys, you too tell me if you think I'm crazy.
18:04 I'm getting to the point where I'm really freaked out about like these kinds of things.
18:08 And especially, you know, people send us stuff.
18:10 They're like, oh, check this out.
18:11 Here you go.
18:12 Like I'm not pip installing those things locally and trying them.
18:15 No way.
18:16 Right.
18:16 I'm going to install them in some isolated environment.
18:19 One thing I've been thinking about doing is setting up my own DevPy server, which is exactly
18:24 the problem sort of that we're talking about.
18:26 So that doesn't necessarily solve it.
18:27 But what you can get with your DevPy server is you can get DevPy constrained, which will
18:31 let you not blacklist stuff or exclude stuff, but you have to whitelist things.
18:35 So you're like, all right, I'm going to try to install, set up this project.
18:37 And when it tells me I need these things and they're failing, I'll make sure they're good.
18:41 Make sure they're used a lot.
18:42 I'll put them in the whitelist and then I'll be happy to just pip install versions, no versions,
18:47 whatever.
18:47 Right.
18:47 But, but sort of being more protective about this.
18:50 I don't know.
18:50 Maybe I'm just paranoid, but this stuff is, it's creeping me out.
18:53 What do you guys think?
18:54 I'm still just having it.
18:55 Let me, I'm still sinking in.
18:57 I don't, I'm not sure how I react to it.
18:59 Yeah.
18:59 My reaction is, I think there's still more infrastructure security wise that has to happen in the community.
19:04 And there's, there's efforts to do signed packages or support in the latest version
19:08 of pip for signed packages.
19:09 And there's also some good hygiene behaviors, but it's true.
19:12 If you want to just try out a package and you just did pip install from a command line,
19:16 you're typically not going to specify a specific version and you're going to get whatever just
19:20 comes off of a pipe with it.
19:21 Yeah.
19:22 We've gone around and around about it internally as well.
19:24 Talking about this because we want to make sure we're not susceptible to this kind of
19:28 an attack.
19:28 And I think good practices like the pip-tools, you know, using that and having pin versions
19:33 has pretty much given us a comfort level with we're pretty safe.
19:36 I mean, no one's a hundred percent safe.
19:38 That doesn't exist.
19:39 But we're feeling pretty good because of the practices.
19:42 Yeah.
19:42 Yeah.
19:43 I know that sounds good.
19:43 I mean, there's only so much you can do, but layers, layers are good, right?
19:46 Layers are good.
19:47 Anyway, this, if you are running, I want to highlight this.
19:50 The ultimate problem highlighted here is that if you have a private PyPI server, that
19:54 there were ways to typosquat on your internal names, not on the public name.
19:59 And there's no way for the public stuff to go, well, you can't have that because it looks
20:03 too close to this, right?
20:04 It might not exist publicly.
20:05 So just be really careful about the versions.
20:08 Be really careful about like whitelisting things if you're doing your own private PyPI.
20:12 And it's important to also note, this is not a Python specific problem.
20:15 So I think some folks may have blown out of proportion, but like other packaging distribution
20:19 tooling all have some similar problems.
20:22 Yeah.
20:22 And I just saw a message on, he was on Twitter or somewhere.
20:25 Yeah.
20:25 This, I mean, obviously npm has this problem, Ruby gems, all these places, NuGet, whatnot.
20:30 Somebody who was involved in like diagnosing and solving these problems was like, please don't
20:35 go post another 4,000 packages to prove your point.
20:38 Just, we are already aware.
20:39 Just send us a message.
20:41 You're causing a lot of work that is like distracting us from addressing this problem.
20:45 So, you know, we don't need more examples.
20:47 We need just maybe a notification.
20:49 Yeah.
20:50 I guess one of the other things is, is that it is typo squatting.
20:54 So we, in our organization, we try to minimize individuals having to type install anything really.
21:00 They, we have, all of our projects have requirements files with pinned versions.
21:05 So they're not going to type the name of anything.
21:08 It's going to have to be in a requirements file first.
21:11 Yeah.
21:11 All right.
21:11 Well, check out the articles.
21:12 There's more details in, in both of them.
21:14 Brian, what you got for us?
21:15 Oh, my turn again.
21:17 Okay.
21:17 It is.
21:17 It is.
21:18 I wanted to talk about something new.
21:23 Adventure, text-based adventure games.
21:25 Have you heard of these?
21:26 I love, I used to play, I used to play Muds when I was quite younger.
21:31 Oh, those were so fun.
21:32 They were so magical, even though they were just text.
21:35 So I actually never got into this.
21:37 but I, I, my, I had entered adventure games.
21:41 What was it called?
21:42 The dungeons of Daggerath, was a game that I had on the, TRS 80.
21:47 And it was, it wasn't, text-based, but the graphics were just lines.
21:52 So it was, we'll go through a cave and, and stuff like that.
21:56 But anyway, a little bit before that.
21:58 So we're talking, in early seventies, so 75 to 77 was a game called adventure.
22:04 and then our colossal cave adventure.
22:07 So you can play colossal cave adventure because Brandon Rhodes has Python adventure.
22:13 And this is just awesome.
22:15 I played this the other day.
22:16 It's so well, I don't know if so fun, maybe like overselling it.
22:20 but it's kind of neat.
22:22 it's a faithful port of the adventure game to Python three from the original
22:27 1977 Fortran code.
22:30 Wow.
22:30 And that was awesome.
22:32 So if I get distracted, it's because I've actually pip installed this and I'm playing
22:36 it right now.
22:37 It's a, lets you explore colossal cave where others have found fortunes and treasure and
22:42 gold, though.
22:43 It is rumored that some who enter never seen from again, like maybe Calvin.
22:47 but one of the things that I loved is I played in both modes.
22:50 So you can, there's two modes you can play.
22:52 You can, in a Python console, you can just kind of run it.
22:56 but you can also, you can also, you can, gonna show for the people watching kind of what it looks like.
23:02 you import adventure and then you say adventure.play and, it has, gives you
23:07 instructions and you have to type things like East, West, get lamp, things like that.
23:11 Oh, it's even like function call style.
23:14 Well, it's function call style.
23:15 If you do the import on the repl.
23:18 if you, if you go through the, there's traditional mode.
23:23 Okay.
23:23 Got it.
23:24 The traditional mode is you do Python dash M adventure.
23:27 And then it's traditional mode.
23:29 You say get lamp with a space between the get and the lamp.
23:32 And that's how I played it.
23:33 But the fun part about this, the traditional mode, it's a 1200 bod.
23:38 So you have to wait for this to type its message to you.
23:42 you may have to explain that to some of our listeners.
23:44 I don't know if I can.
23:47 It's slow.
23:48 So it's sort of ticker tapes out the message to you and you're waiting for it.
23:52 Wow.
23:53 That's impressive.
23:53 I used to be able to identify by sound, the speed of the connection I would get.
23:59 I could tell you is at 9,600 is like 32, whatever, or is it 56 and whether the, and whether the error correcting kicked in or not.
24:07 Yes, exactly.
24:08 You hear it.
24:08 But I don't think I even remember what that sounded like.
24:12 That was some slow business.
24:13 One of the things.
24:14 so, okay.
24:15 So a little bit tie into the, my own personal nerdiness.
24:19 I was curious how this related to Zork.
24:22 So, Zork, I never played either.
24:26 It was a little bit after adventure, but, there was a, TV show called Chuck, that I really liked.
24:32 And one of the premises is this Chuck and his buddy used to play this game.
24:36 And he met this other guy by both of them being Zork nerds.
24:40 And they, they did their own port of Zork.
24:42 And I'm like, is that a made up thing or real?
24:45 And apparently it is real.
24:46 Zork was a follow on to adventure, from 77 to 79.
24:51 so anyway, so I'm, I'm going to ask Brandon.
24:55 So Brandon, can we get a port of Zork also for Python?
24:57 That'd be great.
24:58 Then we'll get our little IOT devices that we can play these adventure games on like a
25:04 little Nintendo switch, but super old school, like low baud rate.
25:07 That'd be great.
25:08 Oh, I want this totally for my Oculus quest so I can do a Texas venture in full VR.
25:12 Well, the 1200 baud, the baud slow down thing is, is entertaining for about 10
25:20 seconds.
25:21 And then I'm like, can I get faster now?
25:24 So yeah, you had the true retro though.
25:26 That was cool.
25:26 Very nice.
25:27 That's cool.
25:27 Awesome.
25:28 All right.
25:29 so for those of you who are Django nuts in the audience, there is a new long-term support
25:35 release coming up for Django three tattoo.
25:37 That's a big deal because long-term support ones are the ones you want.
25:41 Oh my gosh.
25:41 And Django's community is really good about that long-term support.
25:44 I mean, and they have a very good security policy and release revision policy.
25:48 It's very clear, very, very well documented.
25:50 So the next one coming up, which is going to be released here in April is going to be
25:53 3.2.
25:54 this post specifically that I linked to is actually an overview of some highlights of
25:59 interesting features that you may not have noticed.
26:01 You can go read the main Django three, two release page and see kind of the overall new features
26:06 are going to be coming in.
26:07 But this post specifically covered some things that I thought were also interesting.
26:10 a lot of them are performance and kind of, protections against, you know, hurting
26:15 yourself when you're programming.
26:16 So things like covering indexes for Postgres.
26:19 So you can actually, avoid full table scans and do index scans and Postgres, for
26:24 kind of indexes are magic.
26:25 Yeah.
26:26 And then, and so this is enabling even more of the nice magic of those indexes inside of Django.
26:31 Yeah.
26:31 I think it's really cool that it's the LTS release, three, two is coming out.
26:35 I think there's also some async and await stuff in here coming along, which is pretty
26:39 exciting.
26:39 I know that one of the areas that's still pending to get really the async and await stuff
26:44 properly, like full stack is the ORM stuff.
26:46 ORM.
26:47 Yeah.
26:47 So three, two was supposed to be.
26:49 If you wait on the database, that's the thing you need async for more than anything else.
26:52 Yeah.
26:53 And that's kind of one of the notable missing items for me in 3.2.
26:56 I mean, the team is doing an amazing job of implementing all the async features for Django.
27:02 I mean, 3.0, 3.1, you started off with the routing.
27:05 Then you got the views.
27:06 3.2 was supposed to be, I think the ORM included, but maybe just due to the fact that we are talking
27:12 about a long-term support release that that was maybe too risky of a feature to get included
27:16 here.
27:16 But look for that coming soon, like in 3.3 or 3.4 for the ORM, which will be a big, big deal.
27:21 the other things that are included in this 3.2 release, again, kind of focusing on security
27:26 and safety and performance, time zones.
27:29 You know, it's probably one of the two hardest things in programming is the time zones and
27:32 character encoding and off by one, errors.
27:34 so there are going to be some trunk date stuff in here that actually, you know, helps
27:38 you, assign a default time zone in case you didn't put one.
27:41 there's going to be some cool stuff for people who like unstructured data, the
27:44 JSON object DB functions.
27:46 So you'll actually be able to assign some DB functions that can produce, you know,
27:50 JSON mapping type objects or key value pairs where you pass in database functions to operate
27:56 on it.
27:56 there's going to be some cool stuff around signals.
27:58 there's a sin robust, which didn't, log exceptions, but now will.
28:03 So you don't have to, log themes for the admin section.
28:06 Is that coming to this one?
28:07 I know that's something they're working on.
28:09 I don't know on the themes, but I know for the admin section, and this is a common
28:13 thing I've done in the admin is sometimes you want to put computed fields into the admin
28:17 pages for like your, your objects.
28:19 there's going to be a new, what is it?
28:22 There's a new value, not a value expression of the display decorator.
28:25 So you can actually make creating admin feels a lot cleaner.
28:27 The, the kind of syntax for it previously was just a little convoluted if you were not used
28:32 to it.
28:33 And so as a new person, you may not have figured out how to do it very easily.
28:35 So there's a new decorator that actually makes that super, super easy to do.
28:38 there's some other performance things around the database with query sets, with aliases.
28:42 So you can actually create like reusable aliases for things that you're selecting against.
28:46 So you can use them as like filters or like kind of combined statements.
28:49 So it doesn't do two sub queries instead of, it'll do just one, a lot, a lot of cool
28:54 performance.
28:54 And again, these were kind of the less notable, but really kind of important features that
28:58 are coming into a Django three, two.
29:00 Oh, yeah.
29:02 And like, so you can, you can see all the other stuff.
29:04 There's, there's a zillion things coming up in three, two.
29:06 These are just some of the small ones, but there's some of the important ones.
29:09 That's cool.
29:09 Yeah.
29:09 When, when is this coming out?
29:11 April.
29:11 So we should see it next month.
29:12 very soon.
29:13 Yeah.
29:13 Awesome.
29:14 That's great.
29:15 if you're into Django, that sounds really like a big deal.
29:17 It is.
29:18 It is.
29:18 It is.
29:18 All right.
29:19 Brian, anything else that you'd like to throw out?
29:23 Those are all of our items.
29:24 Anything extra?
29:25 No, I don't have anything extra this week.
29:27 How about you?
29:27 Oh, I've got a couple of things I would like to touch on.
29:30 I heard some amazing stuff.
29:32 I heard that Python open source stuff is on Mars.
29:36 Yeah.
29:37 But what I want to say is Python is on Mars question mark, because what I found is if
29:42 you go look at, there's this thing called F prime that NASA open sourced.
29:46 Awesome.
29:46 And if you go over here and you look at it, this is the flight control thing that is for
29:51 embedded them flying, including that little helicopter.
29:54 Awesome.
29:54 it has 16% Python and 44% C++.
29:59 But if you look at the Python bits, so much of it seems to be around the, like the training
30:05 pipeline.
30:06 So my theory is I didn't see any stuff in like the real, like running regular bits.
30:11 I'm thinking maybe it's trained with Python locally.
30:14 And then the models are put on the helicopter and flown with C++.
30:17 If, if somebody knows for sure that Python is on Mars, you know, but details, let me know.
30:23 That'd be awesome.
30:24 I still think it's cool that Python's involved here.
30:26 Yeah.
30:26 All right.
30:27 So that's one quick one.
30:28 Number two, just released a new course.
30:29 And this one is a little different.
30:31 So it's a full web apps with FastAPI.
30:34 And FastAPI is awesome for building APIs, but there's like three or four features of
30:38 FastAPI.
30:39 When put together in the right combination, make it sort of a equivalent framework to what
30:44 you would get with flask.
30:45 So if you're thinking, I would love to use this beautiful API with really nice decorators,
30:50 with really nice async support with Pydantic and all those awesome things that it has.
30:55 But I want to build a web app with it.
30:56 Well, we launched a course on that.
30:58 People can check that out.
30:59 That's really awesome.
30:59 Like basically, I've built some APIs with FastAPI and I need like four or five more pages
31:04 to round out the app.
31:05 Do I have to have a Django plus FastAPI multi deploy thing?
31:09 Like, no, actually.
31:10 And this is all about how do you do that?
31:12 So people can check that out.
31:13 That's fun.
31:13 Super excited about that.
31:14 That's cool.
31:15 Yeah.
31:15 Yeah.
31:15 Thanks.
31:15 Over on Talk Python, I'm giving away five tickets to PyCon, one a week for five weeks.
31:20 So if people want to win a free ticket to PyCon, this year it's virtual.
31:25 So you can attend from anywhere.
31:26 There's not the challenge of, well, I got the ticket, but I need the thousand dollars for
31:29 the hotel, right?
31:29 Like that's not a problem this year.
31:31 So I think it's really cool.
31:32 I decided to run a contest on that.
31:35 The link is in the show notes.
31:36 We got a couple of questions saying, hey, we heard about this live stream because we're listening
31:40 to the podcast.
31:41 How do we get to this live stream?
31:42 This is awesome.
31:43 I think it's fun, Brian.
31:44 I'm enjoying doing the live stream.
31:45 What do you think?
31:45 Yeah.
31:46 It makes it a lot more fun.
31:47 Yeah.
31:47 We get, we get our, our listeners who come in and give us comments and all this stuff is
31:51 great.
31:51 So if you just go to pythonbytes.fm/YouTube right at the top, there'll be upcoming live
31:56 streams.
31:56 And you can say, click the button to remind me of it and so on.
31:59 So that's how you do that.
32:00 Last thing I was on, I got a chance to talk to the medical community and the medical research
32:07 community around Python over on this podcast called the Finding Genius Podcast.
32:11 And it was just a lot of fun to speak about the advantages of Python for like medical researchers
32:16 and folks like that.
32:18 So I'll link to that podcast as well.
32:20 All right.
32:20 Yeah.
32:20 Calvin, anything else you want to throw out?
32:21 I know you.
32:22 I do.
32:23 I wore your, I wore my shirt.
32:25 I know you were fully outfitted.
32:27 So I've actually got two things.
32:28 One, before I get to Python web conference, the DjangoCon Europe 2021 call for papers is
32:33 open until April 1st.
32:34 So if you're interested in talking at DjangoCon Europe, it'll be a pretty worldwide conference.
32:39 It was last year.
32:40 It was a lot of fun.
32:40 We actually did it on the same platform as we did the Python web conference, which is the
32:44 other thing I wanted to mention in the extras.
32:46 So Python web conf 2021 is coming up in about, well, it'll be a week or so after you probably
32:51 hear this.
32:52 March 22nd through the 26th.
32:54 We've got an awesome lineup this year again, even better than last year.
32:57 Michael's obviously back and be speaking at the conference.
33:01 We've got about 60 speakers, almost 20% women.
33:05 There's 43 new speakers this year.
33:07 It's like five.
33:07 Yeah, it's like four or five days or something.
33:09 It's a big conference.
33:10 Yeah, it's five days, but we're doing half days.
33:12 So you don't have to consume your whole day with being in a virtual conference because we
33:16 understand that that is just hard.
33:17 And I think we're all adjusting to what virtual conferences really kind of should be.
33:21 So this is a new experiment, which got four tracks.
33:23 There's app dev, pi data.
33:25 It's an official pi data track.
33:26 There's a cloud track and a culture track.
33:28 So if there's nothing you're interested in, I would be hard pressed to believe that.
33:33 There are tickets for $1.99 for professional, $1.99 for student.
33:36 And we do have our grant program back again this year.
33:39 So we are offering up grants for those who, you know, we want anybody who wants to truly
33:45 attend to be able to, no matter what the financial piece may be.
33:49 So check out the grant program for everyone who buys tickets.
33:52 We offer up grants for those who can't afford tickets.
33:54 And I'm really excited about that.
33:56 You can check that out at pythonwebconf.com.
33:58 Yeah, it's gonna be a ton of fun.
34:00 It was a lot of fun last year.
34:01 We've got a bunch of social events planned and some really awesome sponsors.
34:05 And I'm just super excited about being able to produce something like this for the Python
34:08 community.
34:09 I feel like the web is an area that doesn't always get the attention it should in some
34:13 other conferences.
34:13 And we're hopefully fulfilling that.
34:15 Yeah, super cool.
34:16 It was a good conference last year.
34:17 So I'm looking forward to being part of this year.
34:19 Yeah.
34:20 Yeah.
34:20 Brian and I were just on a virtual conference at PyCascades, which was a lot of cool,
34:24 cool fun.
34:25 We were on that panel about podcasting.
34:27 Yeah, it was great.
34:27 You all might know a thing or two about that.
34:30 We've done it once or twice.
34:31 I'm not sure I would laugh at it, but maybe a joke.
34:33 We could laugh at a joke.
34:34 What do you guys think?
34:35 Yeah.
34:35 Yeah.
34:36 All right.
34:36 So I know we got like two rounds of jokes, but let's do another round of these comments.
34:43 I'm already laughing.
34:45 I know.
34:45 They're so good.
34:46 So I'll do the first one.
34:48 Brian can do the next one.
34:49 Calvin can do the next one.
34:50 We'll just kind of, we got five or six, something like that.
34:52 So it's important to comment your code.
34:54 There's this code.
34:55 I believe it's Java and it is part of a class.
34:58 It says private logger, capital L class logger, variable name logger equals logger class factory
35:05 method dot get logger.
35:06 So private logger logger equals logger dot get logger.
35:08 What does the comment say?
35:10 Logger.
35:11 Quote.
35:11 Yeah.
35:12 Just logger.
35:12 This is a logger.
35:13 Fantastic.
35:14 You passed your code review.
35:16 Yes.
35:16 I guess you have comments.
35:17 Yeah.
35:18 All right.
35:19 Brian, what's the next one?
35:19 Next one looks like C++ comments, but I'm at this block that says this is black magic
35:26 from some stack overflow link.
35:28 Don't play with magic.
35:29 It can bite.
35:30 All right.
35:33 All right.
35:33 Calvin.
35:33 What do we got next?
35:34 Well, this one obviously is a Python comment in the code.
35:38 It says for the sins I am about to commit.
35:40 May Guido Von Razum forgive me.
35:42 Yes.
35:43 I love it.
35:44 Which I would be hard pressed to know what they're getting ready to commit.
35:46 if they read the Zen of Python, they really should know the guidance already.
35:49 Yeah.
35:50 Yeah.
35:50 Yeah.
35:51 Maybe they put a semicolon in there.
35:52 I don't know.
35:53 All right.
35:54 The next one is remove this if you want to be fired.
35:59 Remove the comment or the code below it.
36:02 We don't know.
36:03 Yeah.
36:03 We don't know.
36:04 We don't know.
36:05 Next is a try accept block or catching exception with just a comment.
36:11 And it says, Houston, we have a problem.
36:13 There's no code there, though.
36:15 So you're just, yes, we do have a problem.
36:17 You're just catching a raw exception.
36:18 Don't do that.
36:19 Exactly.
36:19 Exactly.
36:20 All right.
36:21 What's the last one?
36:22 All right.
36:22 The last one here is a definition of int get random number.
36:27 And the body of the function is return four.
36:31 And the comment says chosen by fair dice roll guaranteed to be random.
36:36 If he wants.
36:38 Was this a real code someplace?
36:40 I mean, come on.
36:40 Yeah.
36:41 Oh, there's all sorts of good ones here.
36:43 Yeah.
36:43 They're beautiful.
36:44 One of them that's not on the list is the comment is just, I need to find a better job.
36:48 All right.
36:50 One more.
36:51 Who put this one in here?
36:52 I threw that in there.
36:55 Tell us about this one.
36:57 I'm kind of a card card nut.
36:58 So if you if you kind of exactly like hover over just the first half of the picture, you see a guy in a Ferrari like waving and says, yeah, maybe rolling in the Ferrari.
37:07 There's using Linux and then dot, dot, dot in Windows with WSL.
37:11 And if you scroll down, you see that the Ferrari is actually on a tow truck flatbed being driven someplace.
37:19 And the guy's in it.
37:20 Yeah.
37:20 Like he's driving the train.
37:21 He's cool.
37:22 Very cool.
37:23 Very cool.
37:23 That's funny.
37:24 I'm glad ZDax that you guys like the jokes out there and Dean as well.
37:29 Yeah.
37:30 And just I mean, I commented in the in the chat that you can increase your odds at winning the pike on tickets by laughing at the jokes.
37:37 Yeah, absolutely.
37:38 We'll put you in there twice if you laugh.
37:39 Yeah.
37:40 For sure.
37:40 That's how it works.
37:41 Like the dad jokes of programming here.
37:43 Oh, yeah.
37:44 Of course.
37:44 Yeah.
37:45 We're all dead.
37:46 That's like half our show.
37:47 That's how we all qualify.
37:48 For sure.
37:49 For sure.
37:50 All right.
37:50 Well, Brian, thanks for being here as always.
37:53 And Calvin, thanks for joining us.
37:54 My pleasure.
37:55 I really enjoyed it.
37:56 Yeah.
37:56 Good luck on your conference and catch you next time.