#264: We're just playing games with Jupyter at this point
Watch the live stream:
About the show
Sponsored by us:
- Check out the courses over at Talk Python
- And Brian’s book too!
Special guest: Kim van Wyk
Michael #0:
- Take our survey: Should we try to shorten the episodes? Please fill out the 3 question Google Form here
- We’ll be taking a break so see you in two weeks.
- Also feedback / rate us in your podcast player app
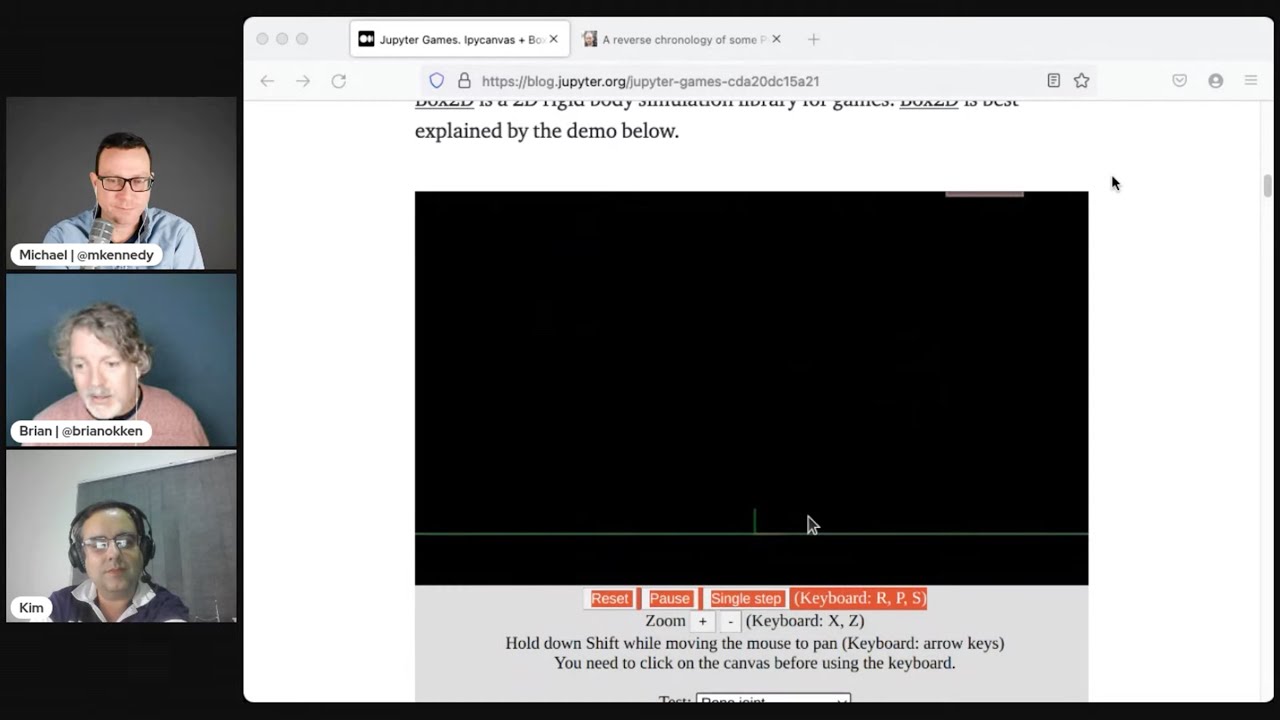
Brian #1: Jupyter Games
- Thorsten Beier
- “Making their own tiny video games can be a great way for kids to learn programming in a playful matter.”
- For 2D physics-based games, Box2D, (written in C++), is a 2D rigid body simulation library
- One Python binding, pyb2d, is from Thorsten
- Game examples use Ipycanvas, Ipywidgets, and Ipyevents for a place to draw and input events.
- There are Box2D examples for physics simulations, like internal combustion and a wind tunnel.
- Game examples, with code, and not that much code
- billiards
- Angry Shapes (like Angry birds)
- World of Goo homage
- Rocket
- Color Mixing (it’s oddly satisfying to play with, and it’s like 73 lines of code, including blank lines and docstring)
- several more examples
- Demo games/examples in binder
- Being able to play with a game engine through Jupyter is kind of amazing. Cool teaching/learning tool.
Michael #2: Canary Tokens
- First, what are canaries (from Thinkst)?
- These tokens might be useful for finding fallout of Log4Shell
- But also generally useful
Kim #3:
- pywinauto and PyAutoGUI - libraries for programmatically controlling a GUI-based tool. These can be very handy for simplifying the use of complex GUIs with dozens of options you need to set every time you run them and also for automating GUI tooling as part of a pipeline.
Brian #4: A reverse chronology of some Python features
- Brett Cannon
- Partly for people wishing for the “good old days” of some old version of Python
- Brett recommends going down the list and stopping at the first feature you can’t live without. If you can’t go very far, better not complain about language bloat.
- I had to stop at 3.10, since I really like the new error messages.
- Here’s an abbreviated list of new features in different Python versions. (And I’m abbreviating it even more for the podcast)
- Python 3.10
- Better error messages, Union operator for types, paraenthesized context managers, match statement (pattern matching)
- Brett notes that
- the match statement required a new parser for Python
- the new parser made better error messages possible
- so, you can’t toss pattern matching without being willing to give up better error messages
- Brett notes that
- Better error messages, Union operator for types, paraenthesized context managers, match statement (pattern matching)
- Python 3.9
- dict support for
|and|=, type hinting generics for built-in collections
- dict support for
- Python 3.8
- f-string support for
=,f``"``{val=}``",:=walrus operator (assignment expressions)
- f-string support for
- Python 3.7
- dictionaries preserve insertion order,
breakpoint()
- dictionaries preserve insertion order,
- Python 3.6
- f-strings, (need we say more)
- also underscores in numeric literals, async generators and comprehensions, preserving keyword argument order
- … goes back to 3.1
- Python 3.10
Michael #5: Hyperactive GCs and ORMs/ODMs
- Does Python do extremely too many GCs for ORMs? Hint: yes
- During the execution of that single query against SQLAlchemy, without adjusting Python's GC settings, we get an extreme number of GC collections (1,859 GCs for a single SQLAlchemy query of 20k records).
- Our fix at Talk Python has been to increase the number of surviving allocations required to force a GC from 700 to 50,000.
- What can be done to improve this? Maybe someday Python will have an adaptive GC where if it runs a collection and finds zero cycles it backs off and if it starts finding more cycles it ramps up or something like that.
- For now, test adjusting the thresholds
- Here are a few presentations / resources:
- Michael’s presentation at Python Web Conf 2021
- Talk Python Memory Deep Dive course
allocations, gen1, gen2 = gc.get_threshold() # GC every 50K not 700 surviving container allocations. allocations = 50_000 gc.set_threshold(allocations, gen1, gen2)
Kim #6:
- DockerSlim- A tool to reduce the size and improve the security of Docker images. I’ve used it a little and got some 1Gb Ubuntu-based images down to 50Mb and that was barely scratching the surface.
Extras
Michael:
- Emojis for comments

Kim:
python -m http.server- a small reminder to people that this is a quick way to get files off a Python-equipped system by standing up a simple web server.- Mess with DNS - Julia Evans released this really impressive learning tool last week to let people explore DNS settings without breaking real sites.
- Magit - a slightly tongue-in-cheek addition to last week’s discussion on git via both CLI and by mashing buttons in VS Code. Anyone using emacs should strongly consider magit for git - I’ve kept emacs open even while trying to use other editors because I find magit so indispensable.
I’ve included these just as small items off the top of my head that may or may not be worth a mention.
Joke:
We use cookies candle (and I don’t care about cookies extension)

- And more Log4Shell memes
Episode Transcript
Collapse transcript
00:00 Hey there, thanks for listening. Before we jump into this episode, I just want to remind you
00:03 that this episode is brought to you by us over at Talk Python Training and Brian through his pytest
00:09 book. So if you want to get hands-on and learn something with Python, be sure to consider our
00:15 courses over at Talk Python Training. Visit them via pythonbytes.fm/courses. And if you're
00:22 looking to do testing and get better with pytest, check out Brian's book at pythonbytes.fm slash
00:27 pytest. Enjoy the episode. Hello and welcome to Python Bytes, where we deliver Python news and
00:33 headlines directly to your earbuds. This is episode 264, recorded December 22nd, 2021. I'm
00:41 Michael Kennedy. And I'm Brian Okken. And I am Kim van Veek. Kim, welcome. You've been on Talk Python
00:46 before, but not here. Yeah, that's right. I've done a couple of TalkBythons with you, including the one
00:51 where you bravely submitted yourself to questions from your audience. The other one, I've taught them
00:56 some small tools. So that was very good fun. I'm very much looking forward to this one as well.
00:58 You know, both episodes you were on were super popular. One was about little automation tools
01:03 and just cool stuff that people can pick up and use easily there. And that was great. And the Ask Me
01:08 Anything was surprisingly one of the more popular episodes as well. So thank you for being part of
01:12 that. And you've been part of the audience. For sure, you've offered comments and feedback as we do the
01:18 live show. And so yeah, to be honest. Yeah. Yeah. But now here you are on stage. Thank you for being
01:25 here. Tell people a bit about yourself before we get started.
01:27 Sure. I am a DevOps engineer at the moment. And also move engineering based in South Africa,
01:33 working with a home loan provider, a mortgage provider in the American sense. I've been probably
01:40 doing Python for close on 20 years. So the fact that I've shaved means you can't see the gray beard,
01:45 but I've been around for a while. That's a great beard. We're going to come back for some good
01:49 jokes at the end about this as well. Not your beard, but just beards in general.
01:54 Oh, great. Awesome. That sounds like really fun stuff. So yeah, thanks. Thanks for being here.
02:00 Now, before we actually get into the main content of the show, Brian, I want to do something just a
02:05 little bit meta. So I went and pulled up or created a question error for people. When we first created
02:12 Python bytes, we're like, all right, it's 20 minutes. The time of this episode is going to
02:16 be 20 minutes. So we're just going to like knock it out you and me real quick. And I think it's grown
02:19 a little bit. We've done, we cover a little bit more detail. We've added a joke. We've added a
02:25 few like little extra things. we brought on guests like Kim and is that, is that still in line
02:31 with what people want when they signed up? So I put together a questionnaire here that just
02:36 asked three simple questions. And I'd really appreciate if listeners could go to the show notes and just
02:40 click, on the link that says this three questionnaire, three question, Google form,
02:45 or, you know, find it on our Twitter account or wherever, but should be in your podcast player
02:48 show notes right near the top. And they can just click that and fill it out and give us some quick
02:52 feedback on idea of having a guest on the link, the show and so on. So anything you want to add
02:58 about that, Brian, just, you know, encourage people to give us feedback so we know.
03:00 Yeah. I'd love to hear feedback because sometimes we feel a little guilty that we're running long,
03:05 but I enjoy the, a little bit more in-depth conversation. We still don't go super deep,
03:10 but I think it's a good, well, I, I, I'm, I'm, I'm flavoring the survey though. So
03:17 forget what I said now. I'd love to hear feedback of what people think.
03:20 Yeah, absolutely. Yeah. So people can give us feedback there. We'd really appreciate it.
03:24 The way people seem to be feeling so far as they, they kind of liked the link. They definitely like
03:29 the guest format. so you're welcome here, Kim, this according to listeners, fantastic.
03:33 Thank you. but yeah, I think, I think people are generally liking, but still like, let's just
03:38 hear from everyone because I'm happy if, if a bunch of the people not in it, you're like, no,
03:42 we really want no more than 20 minutes. And my going on about this is actually making it still longer
03:47 than, then it'd be great to know. Right. So, so we'll go from there. And with that, you know,
03:53 let's, let's play a game. Jump in the first topic. Yeah. I want to talk about Jupyter games and this,
03:59 the idea around, this is, I Python canvas or I pie canvas with box 2d. I'll get a little bit
04:06 more into it, but the gist is, making, making video games and small video games is one of the
04:13 ways that a lot of us, started programming. I know that was the, that was the case for me.
04:19 and there, there were not difficult games, but it was difficult enough. these 2d sort of 2d
04:25 engines and this, some of that's lacking. And I haven't seen that in Jupyter before. And Jupyter
04:31 is an excellent platform for, for a lot of things, especially teaching with, with people
04:37 that don't have computers, if they use an iPad or something like that. So often they can still get
04:41 access to, Jupyter through hosted systems. so this is, Jupyter, this article talks about,
04:48 writing, 2d games and mostly it's a 2d physics engine around, a library called box 2d,
04:58 which is a, a C C++ type engine, but it's something that you can access through Python.
05:04 And the author, yeah, the author, those kinds of physics stuff, you know, when people think of games,
05:08 they think of, Oh, here's what I got to do to get the picture on the screen. Oh, that's just to start.
05:14 Like you need physics, you need collisions. There's like so much stuff that also gets done.
05:18 So this is really cool. Yeah. Things like physics and gravity and collision detection and,
05:23 and, like the examples on this page are great, but the person that wrote it is,
05:29 Torsten beer. And he's one of the, I think he's, he's got a library called PI B2d, which is,
05:36 one of two different, Python accesses to this, this, this box 2d system, but it's pretty
05:45 cool. The, one of the things I like about this article is that talk, it has like lots of pretty
05:51 examples, but game physics engines are, even if they're built for games, they can also be used for
05:57 things like, like, an engine simulation or even like airflow simulations. So there's a lot of
06:05 cool uses for this too, that are outside of games. but the one thing, incredible things is how
06:11 small the programs can be. So, the, this, this article has a, a contained, like an attached
06:18 notebook hosted notebook that, has things like angry shapes, which is like angry birds and a rocket
06:26 game. And there's a color mixing game, which I was just fascinated by. There's like a bunch of colors
06:31 drop into it. It isn't on the, it isn't listed on the, article, but if you go to the example,
06:36 it's kind of color mixing thing. and it's, it's only like 70 lines of code. And, and with that,
06:43 you can have some, some amazing, physics examples. And I'm pretty excited about this actually. So
06:50 I'd like to do, you know, I think this makes a lot of sense in the notebook form,
06:55 because you're trying to visualize certain things and sometimes graphs are fine, but other times
07:00 they just don't capture like flow and that kind of stuff. And it seems like game animation would be
07:06 great. Kim, what do you think? I was also going to say, if you can get something very impressive
07:10 done in 70 lines of code as a learning tool, that's brilliant because that's effectively a screen of
07:15 code. Yeah. Otherwise, you'd be looking at, if you're looking at hundreds and hundreds of lines,
07:19 you know, if you're a seasoned developer, that's perfectly reasonable, but to a new person that
07:23 must look overwhelming. Yeah. Yeah. If you can fit a single screen and say, here is it,
07:27 this is everything you need to make this thing work. And it's quite a powerful tool. And it looks
07:32 like a lot of fun, actually. It does look fun. Yeah. And so there's some interesting,
07:36 the article talks about some interesting, hoops. He had to jump through using, IPy events and I,
07:41 IPy widgets and canvas to be able to draw things and get, events from people. But,
07:49 it's just some fun stuff. Here's like the, I'm sure we're showing on the screen, the,
07:54 thing like angry birds. and to be honest, like the play ability of it isn't maybe like,
08:01 it's not on the level of what, you know, playing an Xbox or something like that. Obviously you
08:06 probably won't hook up a controller and do it. Yeah. But, that you can do something like this
08:12 so quickly is pretty amazing. So I, and also on the other hand, if you write, once you write it
08:16 yourself, the playability actually doesn't matter that much. I think it's looking at interacting
08:21 with the thing you wrote. I think that, yeah. Yeah. I love it. This is really cool. Nice find,
08:26 Brian. All right. Let me tell you about some really interesting cybersecurity side of things.
08:32 So I'm going to first tell you about this thing called a thinkst canary, but that's not actually
08:38 what I want to talk about. It's just to set the stage. Okay. So here's, a challenge,
08:43 something that always stresses me out is what if somebody was to break into your app,
08:48 into your systems, into your cloud infrastructure or whatever, how would you know, right? Like what,
08:54 what would be the indicator, right? If long, if they don't trash it, they don't, you know,
08:58 lock it with a crypto lockers or anything like that ransomware, then they, they could just cruise
09:04 around there. Right. So this company thinks canary, created this, I think you can put it in
09:10 the cloud as like a hosted container type thing, or you can get like a little raspberry pie, like
09:15 things and put them physically on your network. If you had a physical network and you could say,
09:19 you act like a SQL server, you act like an exchange server. You, if somebody tries to search the network
09:24 and says, show me all the active directories, you'd be that maybe we're not even using active directory
09:29 because we're not on windows. But if somebody breaks in, they may well start looking for those
09:33 types of things. And what they'll do is they'll trigger alarms. If somebody tries to interact with
09:37 them and normal things shouldn't, because only if you're like trolling around looking for them,
09:42 should it be discovered? Right. So that's what this is. And with this whole log for shell stuff
09:47 that's going on, it's just such a nightmare of like, well, we installed this app that did
09:52 invoice management for us. Did it have a log for shell vulnerability? I don't know. Maybe they said
09:57 they fixed it. And, but if somebody gets in, it's not just, we have to patch the log for shell
10:02 or the log for j version. We've also got to then know what else has been run because they could have
10:07 installed whatever. Right. Yeah. So the thing I actually want to recommend to Python people is this
10:13 thing called canary tokens. So check this out. This is fantastic. So what you can do is you can get
10:18 different things that will then trigger alarms like emails or other sorts of stuff to you. So I can
10:24 come over here and I can say, I would like to get a URL. And if anybody visits that URL, send me an
10:30 email and say, you know, whatever message I put in here. So I could come in and say, here's a URL and
10:35 send me at Michael at talk Python for my email and say, this is hidden in the admin section unused or
10:44 something like that. If somebody sends me an email, if I get that email, somebody's gone in and click
10:49 that link in the admin section of my site. And if I didn't, it gives you like IP address and all that
10:53 sort of stuff of what comes back. So if I didn't do it, or it looks like an unknown IP, that should be
10:59 highly concerning. Right. So what else that URL is interesting. I can get a DNS token. Somebody requests,
11:05 like does a DNS look up on rollouts.pythonbytes.fm. I can get an alert to that. That'd be pretty
11:13 interesting. A unique email address. If somebody ever tries to contact that, a Word document. So
11:20 you get like a Word document and put it in say like SharePoint or something dreadful like that.
11:24 And if it gets opened, you'll get an email that somebody got that. Let's see, you've got VPN
11:30 wire guards file, you can create a custom EXE. And if somebody runs your EXE or a SQL server instance,
11:36 or you can even do like directly a log for shell link that will run. So if you are trying to like
11:44 figure out, just put stuff in there to let you know if somebody gets into a part they're not supposed to
11:48 be in, like, this is really cool. There's no, it's free. It doesn't cost anything. It doesn't require
11:52 any setup. Like put a Word document in a folder. If it gets opened, let us know. What do you think?
11:57 Well, I was going to say, I've been looking for ways to do exactly this kind of thing because
12:02 you know, it's hardly unique in being concerned that log for shell has got impacts that I don't,
12:08 that I can't see on our systems. Just because your public facing systems happen not to have used log
12:13 for shell things doesn't mean that you're necessarily safe. All it means is that, you know,
12:16 if some other, by some other means, somebody's got into one of your internal systems,
12:20 wouldn't necessarily know that. So I'm very much interested in this. I knew about canaries
12:27 already. I think happened to sponsor the local South African PyCon ZA conference. But canary
12:33 tokens are a very funky additional add-on to that. Exactly. I knew about the canaries as well. I'm
12:38 like, ah, but that doesn't really apply to the world that I live in. I'm not like an enterprise.
12:41 But like this, these make a lot of sense. And they're free, which I think is cool. Yeah.
12:46 Here's what it looks like if you get a notice. It says, this is the email I got. Your canary token
12:52 was triggered. The channel was HTTP. The token was that. This is a test, the IP address of the person.
12:58 So this was one of those URLs. If somebody interacts with this URL, let me know. Here's their user agent.
13:03 Here's the message. There's the IP and so on. So you would just get a notice like that that says
13:08 somebody clicked on something they shouldn't have had access to. Yeah. So anyway, pretty neat.
13:12 Brian? Yeah. I'm not sure. Yeah. It's actually pretty cool. Some of the things I didn't think
13:18 you could, I wouldn't even expect, like somebody cloning your website. I didn't know that was a
13:25 thing. I'm scared now, to be honest. I didn't realize that was something I should be worrying about.
13:31 Get an alert when a MySQL dump is loaded. Like, okay. Like how does that happen? I don't know,
13:37 but that's pretty awesome that it's possible and also frightening. Yeah. Yeah. And Sam out in the
13:42 audience says, ironically, the log for shell might have its own vulnerabilities. You know, that thing's
13:48 been patched a couple of times. It's going to be a big, big problem. Anyway, canary tokens. I think
13:53 this is broadly useful for Python people. You could put the URL stuff inside of your app. You could put an
13:58 email inside of locations. There's lots of stuff that I, like this, the database restore type things and so
14:05 on this, this looks useful. Yeah. So I'm still a little lost. You throw this, like for instance,
14:10 like you said, in the admin section that you shouldn't be using and you just know about it.
14:15 So you don't click it or something. Yeah. So imagine this, imagine you've got in your admin section,
14:19 you've got a, like a search for user button. And then next to it, you could just put a,
14:24 an export all data. Yeah. And then put one of these URLs at the end point at, and nobody who works,
14:31 you just tell everyone never click the export all data. It doesn't do anything.
14:34 But if someone were to break in, what's the first thing they're going to want? Oh,
14:37 let's get the export all data. Boom. They'll go click it and you'll know.
14:40 They're still in, it's bad, but at least they're not in and just have an unlimited time to be in,
14:46 you know? Yeah. You can put some other stuff too. Like let's say you've got a Django website and you
14:50 stick, you load a, like a PHP admin page or something like that. Just at the same URL in case
14:57 somebody's trying to grab that or something. Yep. Yeah. A lot of, a lot of interesting little
15:02 breadcrumbs you can leave in there. Okay. Kim, that brings us to yours.
15:06 Sure. The first topic I was going to talk about are actually two similar, but not quite the same
15:13 pieces of software by Pi Auto GUI and Pi Win Auto are both toolkits for automating GUIs,
15:21 effectively, well, automating GUIs for interacting programmatically with GUIs.
15:25 Pi Win Auto. Which is normally really hard, right? Hey, before you go on, before you go on,
15:29 could you give that like three control pluses?
15:30 Sure. Sorry. I just see now it's a little bit on the small side.
15:34 Thanks. How's that? A little more.
15:36 Space to play with. There you go. Fair enough.
15:38 Well, let me just, while I remember, do it to this one as well. They both happen to be read the docs
15:43 documents. So you're quite right. The programmatically controlling a GUI,
15:47 it can be quite a pain, particularly for GUIs that aren't particularly easy to understand.
15:53 And the reason I bring tools like this up is that there's quite a lot of use cases. I can
15:58 think of two examples at the top of my own career, and I'm sure there's hundreds more,
16:02 where this kind of thing is useful and you might not know it's something you can do.
16:05 And the kind of examples I'm thinking of are particularly in, I'm sure, much enterprise and
16:11 in industrial software, when you get a piece of equipment, you frequently get a GUI tool that
16:17 accompanies it. Probably no API, right? Well, no API whatsoever. There's a tool you fire up and you
16:22 set all the settings, but because the company that supplied you the piece of equipment, they don't
16:26 write software. It's not their thing. They either outsource the tool or the intern writes it. And it
16:32 has 50 checkboxes and laid out in grid form, and you need to set it up every single time you want to
16:38 use that piece of software. There's no ability to remember what you set. There's nothing to do.
16:42 And I've worked with a couple of those systems, and I see, Brian, I think you probably have as well,
16:46 where basically there's a piece of paper next to the computer the software is on with a screen print
16:50 of what the settings should be so that the poor sucker has to come down and use it, knows which
16:54 of the 50 tick boxes to check. And then they have to check that the pattern effectively matches on
16:58 screen, and then they hit run. And something like PyAuto GUI or PyAuto are both useful so that you can
17:04 effectively script the startup of that app. And you can say to, you write a small piece of Python that fires
17:09 this tool up, identifies all the checkboxes, ticks the ones you programmed in, and then either leaves it for the
17:16 human to push go or whatever it is the app does, or for that matter, pushes go itself and then closes the app and
17:20 records that it did that. So that kind of use case is very powerful. And I think there are lots of cases,
17:25 particularly in enterprise software, or internal software that, you know, somebody wrote for the company that does
17:31 something very useful, but it's been around for 20 years. And the guy who wrote it is not around.
17:35 Nobody wants to touch it because the source is terrifying. So nobody's going to sit down and change it.
17:41 How do you even get that Visual Basic 6 or Visual Basic 5 installing it?
17:43 Well, exactly. How do you even compile it now? Exactly. So to be able to wrap it is a very powerful
17:49 thing to be able to do. And the other kind of use case that's somewhat related, it also comes to mind,
17:54 is I've spent a large amount of my career doing industrial automation, factory-based type work.
18:00 And there, the faster you can go and the fewer bits of, the fewer steps you need a human to repeatedly
18:05 do, the better for you in many ways, that the human's time is best spent actually manipulating
18:09 objects and checking things rather than opening pieces of software and clicking boxes and closing
18:13 them again. So yeah, quite frequently, we've had cases on the production line where the vendor of the
18:20 chip we're using has supplied this tool that does some security related thing. And it's a GUI tool.
18:24 And every single time you would have to open it up, you'd have to stick, click the same two boxes.
18:28 They'd have to say, yes, secure this chip, close it again, repeat, wait for another one to arrive at
18:32 your, at your workstation. And if you can automate it again with a wrapping tool, nobody need even be
18:37 involved at all. Part of your production process is you wrap it, you fire up the tool, you click the two
18:42 buttons programmatically, you hit go and you close it again and repeat. And again, I personally have
18:48 encountered situations where that's useful and I'd like to, I would imagine I'm far from alone in it.
18:52 So I just thought I'd mention these things do exist. I suspect lots of people do use them,
18:57 but for people who don't know that they're very useful things to be able to do. You can wrapping,
19:01 wrapping GUIs is, it's a bit tedious upfront because often these tools aren't very well written.
19:07 So you'll have checkbox one, checkbox four, checkbox 27, checkbox 295, and no obvious naming
19:13 consistency with what they do or how they work. But once you've figured it out, let the computer worry,
19:18 let the script worry about what those checkboxes do.
19:20 I've seen the backside of that code where you're like looking at some event handler and it's like,
19:25 if checkbox 24.checked, then do this. Like what in the world? Like who didn't want to name this?
19:33 Because they got a program against those names. That's insane.
19:36 Well, they just do one at a time when you're working on it.
19:38 Well, exactly it. Yeah.
19:39 Yeah. So you're working on one feature and you go, oh, I need a checkbox. Oh, the default is
19:44 checkbox 24. Then you look for the, you do the callback handling and you just, you just did it.
19:49 So, you know, it's 24.
19:50 Exactly. You don't want to bother changing it. That's cool.
19:53 Brian, does this automation have a place in your world?
19:56 Yeah. So there's, there's like, like, like Kim said, there's places where tools that, that don't
20:02 necessarily have a user interface. The, the thing that this doesn't, I don't think these do like web
20:07 stuff, the web automations, other tools.
20:10 Well, I presume you could automate a browser, but I mean, by the time you're doing that, you might as
20:14 well be using the tools designed for it. Yeah.
20:16 Yeah. Selenium or something. What I, what I'd really hope is anybody that has any sort of tool
20:22 that they're writing in, in on a web. So web frameworks often get internal tools get written
20:28 with web frameworks and, and then people forget to throw IDs and things. So the best way to automate
20:34 a web stuff is to have an ID that you can grab onto, but often they're just these, these nested
20:39 div nightmares. But anyway, yeah, there's a couple of tools that we've used by win auto
20:45 for that are, it's pretty nice.
20:47 Yeah. Very nice. Yeah. It seems like if you're building a GUI app, you could test it with this
20:51 right. Sort of full on integration tests from the outside. And also I was talking to somebody
20:56 and they were like, well, this app that I work on, it doesn't have like a concept of a back button.
21:01 So you drive, drive into the menu, hit a thing, go, and then it'll take you back home.
21:05 It's like 10 steps. Right. I could definitely see.
21:09 A little toolbar thing. You press a couple of buttons, like get me to this scenario and I'll
21:13 put the last thing in, get me to that scenario. Like do the nine steps. I'll do the 10th.
21:17 Exactly. Yeah. Yeah. In many ways, the way I've mainly encountered, it has been that the first
21:23 scenario I laid out, not so much actually automating the full running of the tool, but setting the tool
21:27 up so that it is in the right state for what the company needs without having somebody have to either
21:32 consult a document and risk getting it wrong or not know which of the settings they should have,
21:36 because that piece of paper isn't with the computer anymore or that kind of thing.
21:39 It shouldn't happen, but it does. And it's much easier to have this kind of, to have the computer
21:43 worry about what the settings should be. Ideally, the program should remember that, but if they
21:47 don't, they don't. It's not much you can do to change that after the fact.
21:49 It's like external intelligence for a bad app. That's right.
21:53 Well, there's also like API stuff that people forget about. Like, I've got a device that I need to
22:01 automate connecting it to Windows and getting the device set up or something every time I plug one in.
22:07 And just automating that that works sometimes too. So anyway.
22:13 Oh yeah. Absolutely. All right, Brian, over to you.
22:15 Thanks.
22:16 This, I saw this, Brett Cannon wrote an article called a reverse chronological,
22:24 a reverse chronology of some Python features. And I really love this article. It's pretty simple.
22:30 one of the things I like about it is just because we cover so much and we've been covering Python
22:35 releases for quite a while. I kind of forget which releases got, I got which feature in. So a,
22:42 a really brief, you know, rundown of some of the different features is, is nice. Like,
22:48 like last week we were talking and saying, well, well, you're on, if you're on three, seven,
22:52 why would you want to move forward? And I, you know, I can't remember which features in which,
22:56 so having a quick bullet list, like, like in three 10, we got the match statement.
23:02 Of course, we've talked about that recently, but also better, better error messages.
23:06 And I'm going to pause a little bit. Brett brings up in the introduction discussion that if
23:13 you're kind of one of those people that think Python's kind of getting bloated and they're
23:18 throwing too much stuff in it. And I wish that we had the good old days where you could just think
23:22 about all Python in your own head. well, you kind of throw everything out. If you,
23:28 if he said he recommends going down this list and picking the first feature that you don't think you
23:33 could live without. And, and everything before that led to that. So you can't throw that stuff
23:39 out either. It all kind of goes together. And one of the examples is the match statement
23:45 or the, what are they pattern matching that, that was sort of controversial, but the,
23:52 the code to get that to work involved or the process involved, even like making a new,
23:58 parser for Python, or using a new parser for Python. And, but with that new parser, then
24:05 things like better error messages are possible. So, if you like better error messages, which I do,
24:12 that means three 10 and everything below kind of has to stay. but anyway, it's kind of funny.
24:18 The moving on, I, like, I forgot what the dictionary support for, for like, or like
24:24 the or and or equal, that came in in three nine. so if somebody's thinking,
24:31 well, why should I upgrade? this is a good list to take a look at.
24:35 Nice. All right. I did the little exercise. I've decided three, seven, three, seven for you.
24:39 So what was the thing in three seven that you can't live without?
24:42 So the dictionary preserving order stuff is really nice for like reading and writing files
24:48 and making sure that they don't, diff hard. You know what I mean? Like if you try to like,
24:53 so they're in the order, you put them there, all the other stuff I'm not hating on it. Like I like
24:56 the walrus operator. I like some of the other things. I like the lowercase list bracket int
25:01 rather than importing types. All those are great. I'm not knocking them. I just saying like, where would
25:05 I go? Oh, this, it starts to hurt where it really starts to hurt for me at three, seven and below.
25:11 Well, I was, I was trying to Jupyter, like Jupyter, an interactive Jupyter system the other day,
25:17 looking at some data science stuff and it was already set up. And I tried to throw in this,
25:21 the F string value equal thing to be able to quickly debug a item and it didn't work too soon.
25:28 What the heck? And it turned out it was using three, seven and not three, eight.
25:33 and apparently I'm very used to that. and I don't think I could live without it. but,
25:38 and then, reminder also that, three 11 when it comes out in a year, it's,
25:44 there's going to have a lot of speed ups. So yeah, if that comes up with a lot of the performance
25:47 stuff, then like, that's my new number. If you forced me to roll back, I would refuse to go
25:54 further than 3.6 because I must have those f-strings. Yeah. Yeah. Cause I basically it's so much,
25:59 much that just make your code so much more attractive. That said, while I don't necessarily
26:04 use everything that comes in the new versions, I don't particularly have any problem with them being
26:08 there. I'm quite happy to just use the parser Python I want. And, what really happens to me is that I
26:13 don't necessarily know I can do something until two versions later. I probably only started doing
26:18 that value equals on 3.9, for example. Yeah. And mainly cause that's probably the first time I
26:22 needed it more than anything else. Not, I don't particularly rush forward and use the new features
26:27 when they're available, but I'm glad they're there when I do ultimately want them. Yeah.
26:30 Three, six is an interesting example you bring up because, it's got f-strings. It's got a whole
26:35 bunch of other stuff too, but really we can stop with f-strings. pretty much. Yeah. Yeah. Yeah.
26:41 And then the debugging stuff, Sam and audience says, yes, F curly bracket name equals is
26:47 indispensable for a debug. Oh yeah. I'm, I'm with him. As I say, I hadn't used it when it first became
26:51 available, but I would really not want to not have it available now. Yeah. I'm a caveman print debugger.
26:58 So yeah. Kim, I like your, your take on it. Like it's not going to hurt me if I don't care about it.
27:03 I think one of the powers of Python is that you can be very successful with Python with a partial,
27:09 quite partial understanding of what it even is. You don't need to know what a generator is,
27:14 what a yield is like, what an expression is, what a class is, maybe not even how to create a function.
27:19 Just, just write the code top to bottom and it'll probably still do something for you.
27:23 And so you can sort of bring these in when it makes sense.
27:27 Yeah. I would definitely still not teach match statements to beginners. It's unnecessary.
27:32 No, so yeah, totally agree. Whereas I would use if strings, for example,
27:36 for a beginner because it's just so much more readable than the other stuff is. But yeah,
27:40 you're right. You don't have to magically, you don't have to use it all because it's there.
27:43 Yeah. I'm sure there's people out there who feel like it's, I got to use it. It's here.
27:47 But no, I agree with you. All right. How about we talk?
27:50 I don't think I've ever written a wall-less operator, for example. Sorry.
27:52 You're saying. Yeah. I actually, I actually took down a Talk Python website or the training website, one of them with the walrus operator, because I put the walrus operator
28:00 in a utility script that's not actually used by the site, but the site scans all the files trying to
28:07 figure out where the handlers, the view methods are. And it killed it because I forgot that this is way
28:12 back when it was still running 37. So that was my first really, oh my gosh. But yeah, now I use it.
28:18 It's good. All right. So I want to talk about something that I've actually personally been working on
28:22 lately. This is a follow-up to a Talk Python episode I did where I interviewed Mike Baer,
28:29 came on and did a great job, talked about SQLAlchemy 2 and so on. And I mentioned that,
28:35 you know, just the way that Python's GC is set up is it's somewhat hostile to things like ORMs,
28:43 where they have to create a bunch of objects and return them to you in one batch. And what do I mean
28:49 by that? Well, if I'm going to do a query and it's going to return a thousand records,
28:54 like the best case scenario is it has to create a thousand classes, SQLAlchemy models, and give
28:59 them back, right? If I'm asking for them as a list. Well, the way the GC and Python works,
29:04 not the reference counting, but the garbage collector is after 700 allocations of container types,
29:09 classes, dictionaries, lists, et cetera, that do not get cleaned up 700 surviving over the cleanups
29:16 over a period of time. That's going to trigger a garbage collection. And so I said, ah, you know,
29:20 like, is there something you could do? Is there something we could like kind of think about with
29:23 ORMs? This is not at all specific to SQLAlchemy. This is happens. I have an example here called
29:29 Pythons GC and ORMs as a app and a little conversation on GitHub. And I said, is there something we maybe can
29:35 do? Or have you guys thought about it? Because I don't really sure what the answer is. And said,
29:40 not, not so much sure, but here, check this out. So I created this app. It creates a thousand records
29:46 in both a SQLite database and a MongoDB database. So we have like two really different examples.
29:51 And then you run a query that returns 20,000 records. It's probably a lot.
29:55 Yeah. Just an estimate. You've been in next 100,000 records.
29:58 Yeah. If I didn't say that a hundred thousand records in the database and it gets 20,000 of them back.
30:03 Okay. It's probably a little extra, but for example, if you go to, you go over to the talk Python
30:09 training site over here, we've got a site map. And in this site map, there are many, many holding down
30:17 the page down arrow and you barely see it. We've got to get like 5,000 records, 6,000 records just to
30:23 to like list out the number of the pages that contain transcripts for the site map. Right?
30:28 So it's not entirely unreasonable. You would get a bunch of records back and then do something like
30:33 render a page with it. Right? Well, under this scenario, if you just run straight Python,
30:39 that single query results in a hundred, 1859 garbage collection runs just to get one answer back.
30:48 Is that insane? None of which is garbage. Yeah. No, it's not garbage yet because it's just being
30:53 realized from the database, right? Like it, it hasn't even come into existence all the way yet.
30:58 And it's just like garbage, garbage, garbage, garbage, garbage, garbage. And it takes 900 milliseconds.
31:04 If you go and you tweak it in a way that I described here, which you may or may not want to do, but if you
31:09 did, if you tweak the garbage collector, it will go from 1,800 collections to 29, 64 times less. The speed
31:18 of the program is 23% faster. Okay. But it also uses less memory. Okay. Less garbage collection.
31:26 Less, lots less garbage collection. And it's not just 1,800 versus 29. Python has this 100 to 10 to 1
31:36 ratio of Gen 0, Gen 1, and Gen 2 collections. And Gen 0 collections are pretty cheap because it just
31:42 touches new memory and looks at it. Gen 1 looks at like stuff that's only been inspected once. And Gen 2
31:48 inspects the entire memory space for it to see, right? So this one, this one will also trigger,
31:54 how does that? 185. Yeah. 185 Gen 1. So 18 Gen 2s, right? So it's not just, oh, there's fewer.
32:04 There's also like this, this other 29 here, this is zero Gen 2 collections, very likely, right? So
32:09 it's not just the number. They're also like cheaper than doing that. So this is pretty interesting. What
32:16 do you got to do? You just say you run less frequently on allocations and then leave everything
32:22 else alone. Does it make a lot of sense for absolutely everything? Probably not. There's
32:26 probably some scenario with lots of cycles that this is a problem. But anyway, this, this is an
32:32 interesting thing to sort of consider if you are doing some kind of API or a website or something
32:38 that queries a lot of data over 700 records, basically, you're going to absolutely encourage GC when
32:44 you know it's not garbage, right? So I don't know. I thought this was interesting. I'll put it out there
32:50 for people to play with and get some feedback. It should be fun to hear about it. I think this is very
32:56 interesting. And I, I'm going to, I mean, I plan on playing with the garbage collection myself. So I'm glad you
33:02 have this little sample app thing up to, to start playing with it. One of the things that you can do that a lot of people don't mess with too much is, is not, not slowing down the frequency,
33:14 frequency, but you can disable it and enable it. And I'm not sure. I'd like to play with that a little bit more to see if you can kind of kick it off or something like that, because you can disable and you can call GC collect if you need to. So like it's, it's there. I'm not sure if it makes sense to do it, but the switches are there.
33:34 Yeah. I mean, there's, I mean, there's times where, I mean, you're not going to get real time with Python, but you can, you can get, there's times where you know that you're not doing anything else. So garbage collection is fine. And there's times where you're doing an event and you really want to get done with this as fast as possible. So it might make sense to turn off GC.
33:52 And for people who are not super focused on this, turning off garbage collection or altering garbage collection only affects a very small portion of Python's memory because the primary way is reference counting.
34:04 So reference counting things stop referring to it. It goes away only in the case where there are cycles. Does GC even apply? Right. So that's actually, unless you've got really interesting algorithms that are super focused on that kind of stuff, you know, you probably don't even have cycles or very rarely do you.
34:20 Yeah. Interesting. It's the one size fits all solution, but where it does fit, it's a pretty simple thing to do that really makes a heck of a difference.
34:28 Yeah. It's, it's, it's quite interesting. So my, using was, well, maybe someday Python will have an adaptive GC where it runs a certain number of times and says, oh, I ran, but I didn't actually find any garbage, any cycles.
34:41 So let me back off that threshold by a factor or two. And then I didn't find any garbage again. So I'll back it off. And then I'll look, I found a bunch. So now we got to start doing this more frequently. And I could see like an adaptive garbage collector turning these numbers. But until then I just cranked it up. Yeah.
34:57 Interesting. All right. Yeah. Kim, you want to take us out of here for our main topics?
35:01 Sure. the other topic I was going to talk about is a tool called Docker slim, which basically.
35:07 It already sounds good. I don't know what it does, but.
35:10 The opposite of Docker slim.
35:11 I want my docker to be slim. Let's do it.
35:15 It's effectively, as far as I can tell, well, not quite magic, but it certainly seems like it. I use Docker quite extensively at work and because I used a fair amount of it at work, I started using it for a lot of personal stuff.
35:27 as well. And the websites I deploy in my own right and little things running my own systems are all in Docker containers.
35:33 And unless you, you take a lot of care about it, your Docker images can end up quite large. If you start with just a Python in an Ubuntu base, for example, you're probably looking at about a gig of Docker image.
35:44 before you get anything done.
35:45 Now the way Docker works, unless you have just one of those things, if you've got more than one, you start to benefit from shared layers.
35:52 So you're not having a gig and another gig and another gig, et cetera, but still it all kind of adds up. Docker slim is a tool to basically look at your existing images, do some analysis and give you back a much smaller.
36:03 And in many ways, much more secure image.
36:05 I have run this, I read, earlier today, just to kind of check that I wasn't misremembering from the last time I used it.
36:12 And I fed it an image I had, which was an incredibly simple, small little floss API app I had written.
36:19 And it would had one job.
36:20 It basically, whenever you sent anything to an endpoint, it printed out what that was, forget exactly why I needed that.
36:26 I think I was having trouble figuring out some suppliers that it wasn't documented how some suppliers web book was going to work.
36:32 So basically I set this up and I said, talk to me and then looked at what it said.
36:35 Exactly.
36:36 Side note.
36:37 That's way better than trusting their outdated, crappy, inconsistent documentation is just, all right, why don't you just call it?
36:44 We'll just print out the JSON document.
36:46 Exactly.
36:46 Yeah.
36:46 And then we'll go from there.
36:47 Yep.
36:48 So yeah, as a, as a side note, that was quite an easy thing to do, but, that was, I just put that into a, an ability based container running,
36:56 I forget exactly what, presumably I was using FastAPI.
36:59 So it would have been Python and Ubuntu and FastAPI and et cetera.
37:03 And that was about a gig of, of image.
37:05 I fed that to Docker slim and I ended up at 48 mix.
37:08 and it still worked.
37:10 It did everything it was supposed to do.
37:11 Granted, I fed the simplest thing I had.
37:13 I mean, at one end point and so forth.
37:15 I had, there's a lot of dependencies.
37:17 There's Python.
37:18 Exactly.
37:19 There's flask.
37:20 Maybe there's even micro whiskey or something running there.
37:22 Who knows?
37:23 But yeah.
37:23 Well, exactly.
37:24 what it has done is it's closed down all sorts of other angles of attack mixed sound a bit dramatic, but all sorts of ways that you could interface with the container that you don't necessarily need.
37:33 It no longer has, for example, a, bash is no longer available in it.
37:38 You can't run it in interactive mode and talk to it, which is not necessarily a 100% positive thing.
37:44 It makes debugging a bit harder, but they do have some solutions for how you can do that with side containers and talk to it in other ways and the like.
37:51 And they, if I, if I go through the documentation, effectively they're doing all the security stuff and the app honoring stuff and all sorts of things that I know are important, but I don't know enough about to do right.
38:01 I don't trust myself to do those things correctly.
38:02 I can basically follow someone's suggestions, but I have absolutely no way of knowing if the suggestions I'm following are valid.
38:07 I'm not immersed enough in this world to know what the best thing is to do.
38:10 So I'm much happier to have somebody come along and say, we've written this tool, we get the stuff.
38:15 we'll do the best we can to make it more secure.
38:18 Even if it isn't a hundred percent secure, it's far better than I was going to achieve my own.
38:21 And, it's, it's, I haven't used it enough to get a 100% recommendation that this will fit every use case.
38:29 I'm sure like every tool is there's things that does well, there's things that doesn't do well.
38:32 There's some use cases where it's maybe not so suited, but just from a little bit of experimentation with it,
38:37 it looks like something I'm going to be inserting into my tool chain where I can, because the smaller the images are, the better, really.
38:43 Especially if we're all working from home, we're putting these things down from servers that aren't actually in the building that you're in anymore.
38:49 And if you're doing a continuous deployment, which means pushing those actual images, then you want to build that quicker.
38:57 Well, exactly, yes.
38:57 Yeah.
38:57 Yeah, cool.
38:58 Very nice.
38:58 Yeah.
38:59 One of the things that Docker's used for the, I think a lot of web people don't think about, is, cross compiling.
39:06 That's, one of the places where Docker shows up and it's one of the places I use it is to compile on a machine that I don't have access to.
39:14 So I can have a Docker image, like I can have a windows machine with a Linux Docker image or something, and I can do compiling in there.
39:21 So slimming that down speeds up my compiles, or I conceptually would.
39:27 So I think this is something that definitely to try if you're using, using that.
39:31 Exactly.
39:32 You've reminded me of, in a similar vein, Docker is the basis of, continuous integration systems.
39:38 the ultimate end result is built inside a Docker container with all the bits we need.
39:44 That can take quite a while because it can be quite large.
39:47 If you can slim that down as well, you know, the faster you'll see, I, is the better for you, really.
39:50 Yeah, always.
39:51 Yeah, absolutely.
39:52 All right.
39:53 Well, Brian, I think that might be it time for some extras.
39:56 Oh, I do want to do a quick followup.
39:57 I thought these were extras, but they're actually not.
39:59 They're, things that, that I do want to point out really quick.
40:03 I actually gave a talk on this whole memory thing.
40:05 If that GC conversation sounds interesting to you over at the Python web conferences here.
40:10 So people can check that out and also have a talk Python class that like dives into a whole bunch of this stuff.
40:15 Nice.
40:16 I meant to include that in the before thing.
40:18 Now we're at the extras.
40:19 Let's talk about that.
40:20 What do you got?
40:20 the only thing, one of the things I want to shout out is to everybody that supported, the pytest book.
40:28 So, I pragmatic, pragmatic.
40:31 If you just go to the main page, there is a, best sellers link, that has had, Python testing with pytest on it for many weeks now in the top six.
40:44 And I just wanted to thank everybody that supported the book and, and helped, the success of this.
40:50 Also the feedback that I got, of the technical reviewers and plus many other people going through and submitting a RADA is going to make this a really solid book.
40:59 And I'm really, just happy to be part of a community to put this together.
41:02 So thanks.
41:03 Yeah.
41:03 Congratulations.
41:04 That's awesome.
41:04 Kim, you got anything extra you want to throw out there?
41:06 A couple of small things.
41:08 As I was hoping to mention, if we had the time, I see we've actually got mess with DNS up on screen.
41:13 This is a good place to start.
41:15 I started to mention this little website, mess with DNS.net, which Julia Evans, who, on Twitter is balk.
41:22 and you produces a variety of excellent webzines and so forth.
41:26 I think you've actually, you've discussed her get, learning webzines before.
41:30 Oh, blank.
41:31 Get.
41:31 That's the one.
41:32 Yeah.
41:32 and I think there's an HR friendly one whose name I can't remember.
41:36 Oh, shucks.
41:37 Get.
41:37 The memorable one.
41:38 Yeah, exactly.
41:38 Oh, something like that.
41:40 She released, something I got, yeah.
41:42 She released mess with DNS.net recently as effectively a way to play with DNS without breaking your actual website.
41:49 which isn't something I'd ever thought to, to look for, but now that it's around, it's actually a brilliant idea.
41:55 There are some hard to understand things based into DNS and what isn't a record in a CNAME and what, you know, if your TTL is a three digit number versus a five digit number, what's the difference?
42:06 Or for that matter, what does TTL mean?
42:07 And it's not necessarily an explainer for all these things, but it is a way to make these settings and see what they do without actually breaking a real website.
42:15 So effectively she's spun up a sub domain, with a signed name.
42:20 This one I happen to be on is goblin61, mess with DNS.com.
42:23 The worst you can do is break goblin61.mess with DNS.com.
42:26 And that will then just go away when the next person comes along.
42:28 so it's actually a really smart, really clever idea.
42:31 typical to Julia's thoroughness.
42:33 She's got a series of experimental suggestions on the side.
42:36 Here are some things you can try.
42:37 Here are some tutorials.
42:38 How about making a CNAME?
42:39 Or here are some weird things you can try.
42:41 What happens if you've got a very long TTL or you convince three different DNS servers that your sub domain has three different IPs.
42:47 Why you would do that is a mystery to me.
42:49 But you know, what would happen if you did is something you can explore with this site without actually breaking your real website.
42:55 And this seems like a very useful learning tool.
42:56 Yeah, absolutely.
42:58 Cool.
42:58 I love it.
42:58 That's fantastic.
43:00 There were one other, two other small things I just wanted to mention one just because I use it all the time and I don't know how common knowledge it is.
43:07 It is possible in Python.
43:09 And I don't have a web page to open for this to run a small little web server.
43:13 If you do Python dash M, what's it?
43:16 HTTP dot serve or dot server.
43:19 I've gone blank on which it is now, to be honest.
43:21 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:22 .
43:23 Yeah.
43:23 Yeah.
43:23 Yeah.
43:23 I'm reading your notes.
43:25 I don't actually.
43:26 I'm just going back to the notes to have a look myself.
43:28 Yeah.
43:28 That effectively fires up a web server in the directory you opened it in and serves up the files that are there or the sub directories that are in there.
43:35 And there's no security, there's no attractiveness, there's no styling, there's no anything of the sort, you wouldn't serve this to the public.
43:41 But if you wanted to get a file off the machine, and I do this quite a lot to get files onto my phone, for example, firing up a web server there and then and just pointing by the script or your own, you know, just to send your browser to your local host with the port you gave it and just download the files from there.
43:57 It's a useful thing to be able to do.
43:58 Yeah, that's a cool trick.
44:00 .
44:00 It's like a directory browsing, basically.
44:02 Yeah.
44:02 Exactly.
44:03 And then the final little extra I just wanted to talk about, and this is a little more tongue in cheek, somewhat.
44:08 In both last week's Python Bytes and on recent talk Python episodes, you have been speaking a little bit about different ways of doing Git.
44:16 You were discussing doing all your Git on the CLI.
44:19 And I think one of your audience members at the last Python Bytes suggested the way they do Git is just mash all the buttons they can find in VS Code.
44:27 There is, I just want to put out there, there is a middle ground that you could be looking at.
44:32 There's a tool called Magit, M-A-G-I-T, which is effectively, if you're an Emacs user and you don't know Magit, you should change that immediately.
44:41 Magit is effectively a brilliant way of doing, to me, a brilliant, indispensable way of doing Git inside Emacs.
44:47 And then you should learn Emacs.
44:48 Granted, it doesn't mean you need to learn Emacs, but in just a couple of short years after that, you should be an expert at, you should find Magit indispensable.
44:56 It'll take you a couple of years to learn Emacs.
44:57 I'm not disputing that.
44:58 But once you've got the Emacs down, Magit really is an excellent option to look at doing your Git with.
45:04 So if you're tired of doing it on the CLI, just set some years aside.
45:06 Learn yourself some Emacs.
45:06 Turn to Magit and then wonder how you ever did anything else.
45:11 Set some years aside.
45:13 I don't think that's fair to Emacs, but just a little bit too much.
45:20 I'll concede Emacs as a much longer learning curve than VI, but it's not Gears.
45:25 And I say this, I mean, yeah.
45:28 Yeah.
45:29 And Mario and the audience are taking credit for the VS Code button matching.
45:33 Right.
45:34 Right on.
45:35 Cool.
45:36 Yeah.
45:37 That's a great recommendation.
45:38 All right.
45:39 Is that it for your extras?
45:40 Go ahead.
45:41 In terms of being unfair to Emacs, I've been using it for more than 20 years and I find
45:44 it almost impossible to use anything else, but I'm sure it didn't take me years to learn.
45:48 It's just been a long time.
45:49 That's right.
45:50 Yeah.
45:51 Well, all right.
45:52 I got a few throughout the room.
45:53 Actually just one.
45:54 I made a comment, I think on the last show, Brian, about using emojis in my code.
46:00 Yeah.
46:01 So I wanted to bring that example up.
46:02 So here's like a little CMS thing that I got going on.
46:05 And if you return a collection, like themes are represented by these little tags in the CMS.
46:10 And if you return a collection, the comment has a list of emojis.
46:13 And if you return, if they're just like processing a single thing, you get that emoji.
46:18 For pages, you get a list of page emojis and so on.
46:22 Anyway, that's what I had in mind when I talked about that.
46:24 That's pretty cool.
46:25 Yeah.
46:26 You can sort of just scan through.
46:27 Oh, look, there's a list of these.
46:28 This must be do a bunch of stuff.
46:29 Or I don't know.
46:30 I could probably come up with something like a modifying.
46:32 I'm going to change a theme versus read a theme or something like that.
46:36 Yeah.
46:37 Anyway.
46:38 Well, that brings us to the laughs.
46:39 And I hope you all enjoy schadenfreude because it's bad this time.
46:44 Thank you, Log4J.
46:47 Okay.
46:48 So let's see.
46:49 First of all, this is not schadenfreude.
46:51 This is just something about the cookies.
46:52 My daughter yesterday gave me this candle.
46:55 It has a website.
46:56 We use cookies to improve our performance.
46:58 And then me, same.
46:59 I just eat cookies.
47:00 I thought that was really just funny for like a tech candle.
47:03 It should be a 10 of cookies though.
47:06 I know it should.
47:07 It absolutely should.
47:09 At least it should smell like cookies.
47:11 It says scented.
47:12 I have no idea what scent it is, but it better smell like.
47:14 Does it smell like websites?
47:15 Maybe.
47:16 Maybe.
47:17 And then I just want to point out more practically.
47:19 I have this add on you can get for all the browsers.
47:21 I don't care about cookies.
47:22 And if it sees one of those cookie warnings, it'll try to click it and just accept it.
47:26 Oh, this is indispensable.
47:28 Brilliant.
47:29 Absolutely.
47:30 And then Brian skin starts us off with the log for J stuff.
47:35 So if you remember, if you're aware log for J a lot, the problem with log for J is if
47:40 you try to log a piece of text, even as an argument, if that text has J and D I
47:47 colon L a D P L a L D a P colon slash slash to some Java library, instead of logging it,
47:55 it will execute that Java stuff.
47:57 Even if it's remotely on the internet, it'll output the result of that.
48:01 Like you're hacked or whatever.
48:02 Right.
48:03 And so we've all heard of the little Bobby tables, right?
48:06 Here's the modern day one.
48:08 Hi, this is your son's school.
48:10 We're having computer trouble.
48:12 Oh dear.
48:13 I'm going to break something.
48:14 Well, in a way, did you really name your son, you know, dollar curly J and D I colon L D a
48:21 P colon slash slash evil corp.
48:23 Parenthesis, parenthesis, Bobby.
48:25 Oh yes.
48:26 Little Bobby Jindy.
48:27 We call him.
48:28 Well, we've got our servers crypto lock.
48:31 I locked.
48:32 I hope you're happy.
48:33 I hope you've learned to synthesize your log for J inputs.
48:36 Isn't that fantastic.
48:37 Yeah.
48:38 I have a feeling.
48:39 I mean, this is going to go on.
48:43 It'll be the next.
48:44 It isn't log for J.
48:45 It'll be something else next year.
48:46 Yeah.
48:47 And well, I mean, it's been, it's been there for 10 years.
48:50 Exactly.
48:51 Yeah.
48:52 It's not a new thing.
48:53 Unfortunately, it's not even a vulnerability.
48:54 It's just, wait, you can actually do that on purpose.
48:57 It's a feature.
48:58 And Brian helpfully suggests this actually came from log for J memes.com.
49:04 So we got to go there for a second.
49:06 Well, of course that exists.
49:07 Of course.
49:08 And oh my gosh.
49:09 Like, look at this picture.
49:10 So Brian, we described this person for me on the screen.
49:13 There's a person in a saying next to him.
49:15 Old white guy.
49:16 like to me, he looks like a perfect sort of grandpa sort of character, right?
49:21 Getting up there, probably 70, you know, nothing wrong with a guy, but it says upgrading
49:26 log for J three times.
49:27 It wasn't that stressful.
49:28 Dave, 28 years old.
49:30 What else have we got in here?
49:34 We've got, I wish that was outrageously funny and not just kind of true-ish, but yeah, I
49:38 know here's like a 1940s looking picture, like a dad and some kids hanging around.
49:42 Daddy, what did you do during the great war?
49:45 the log for shell incident.
49:47 let's see.
49:48 There's a few of you go in here.
49:50 Like there's the, how many days since such and such accident?
49:54 Zero days without log for J CVE.
49:57 And there's like Homer running around with like a nuclear glowing stick.
50:00 you can just spend, you can spend some time in this place.
50:03 It's, it's probably unhealthy.
50:05 There's like a grim Reaper.
50:07 Just going through taking out technology.
50:09 And it has a log for J on the grim Reaper.
50:11 You know?
50:12 let me see if I can find one more that there's, there's some really good ones.
50:17 this one is probably good.
50:19 There's a picture of a guy in a tuxedo.
50:21 It says vendor, not vulnerable to log for J, but there's a mirror and you see the back
50:24 of him.
50:25 His clothes are just all gone.
50:27 It says use it.
50:28 Yeah.
50:29 Yeah.
50:30 That one's pretty gross.
50:31 I want to get that.
50:32 But yeah, there, these are, these are just fantastic here.
50:36 so anyway, people can check out the memes.
50:39 Thanks Brian for sending that in Brian skin.
50:41 Yeah.
50:42 I am reminded.
50:43 I did see one the other day.
50:44 I don't know that I could put it up now, but it's effectively that I just seen it in
50:47 various other means, a chap receiving an award from probably his manager.
50:50 So, you know, me receiving an award from the manager for not being vulnerable to the log
50:54 for J vulnerabilities and the inside thinking let's mainly cause I chose not to log in.
50:58 Yeah.
50:59 I completely forgot to log anything.
51:01 Exactly.
51:02 Oh, that's really good.
51:03 Yeah.
51:04 That's a tweet today.
51:05 Java runs on billions of devices is not a statement of pride, but a statement of pure
51:09 terror.
51:10 Yeah.
51:11 All right.
51:13 Well, I don't want to hit on, Java too hard, but the log for J I just cannot believe
51:19 somebody thought it's, it's a fantastic idea to execute remote code that you cannot escape
51:24 from a logging system.
51:26 Yeah.
51:27 In a logging system.
51:28 It's just, what did you think you would get?
51:29 So here we are.
51:30 Yeah.
51:31 With log for J memes.com.
51:33 If you want to scroll through it.
51:34 Let's back up and say somebody thought writing an application in Java was a good idea.
51:40 No, sorry.
51:41 I'll get hate mail for that one.
51:46 So.
51:47 Yeah.
51:48 Don't mail Brian.
51:49 Don't email Brian.
51:50 He knows.
51:51 All right.
51:52 Well, so Brian, that's it for the year, isn't it?
51:54 It is.
51:55 It's the last episode.
51:56 We're going to take a little bit of time off.
51:57 Yeah.
51:58 Some well-deserved time off.
51:59 Yeah, absolutely.
52:00 So thank you everyone for listening.
52:03 Kim.
52:04 Thanks for coming to join us this time.
52:05 Brian, as always.
52:06 Thank you.
52:07 And we'll see everybody next year.
52:08 Yeah.
52:09 See you next year.
52:10 Thank you for having me, guys.
52:11 That was, that was brilliant.
52:12 Yeah, you're welcome.
52:13 If you're out there and you still haven't filled out that form and given us our feedback,
52:16 let us know.
52:17 The Google form link is at the top of the show notes.
52:20 All right.
52:21 Bye.
52:22 Cheers.
52:23 Thanks for listening to Python Bytes.
52:24 Follow the show on Twitter via @pythonbytes.
52:27 That's Python Bytes as in B-Y-T-E-S.
52:30 Get the full show notes over at pythonbytes.fm.
52:33 If you have a news item we should cover, just visit pythonbytes.fm and click submit in the
52:38 nav bar.
52:39 We're always on the lookout for sharing something cool.
52:41 If you want to join us for the live recording, just visit the website and click live stream
52:46 to get notified of when our next episode goes live.
52:49 That's usually happening at noon Pacific on Wednesdays over at YouTube.
52:54 On behalf of myself and Brian Okken, this is Michael Kennedy.
52:57 Thank you for listening and sharing this podcast with your friends and colleagues.